我好菜啊啊啊
Web
nisc_easyweb
题解
- 使用 dirsearch 扫描目录,发现 robots.txt
- 访问 /api/record/ ,得到 api_test.php
- 访问,查看源代码,找到 hint
- get 参数,得到 flag
吃豆人吃豆魂
题解
- 访问网站,查看源代码
- 在 index.js 中发现 alert 函数与 经过 base64 加密的 flag
- base64 解码,得到 flag
Misc
checkin_gift
题解
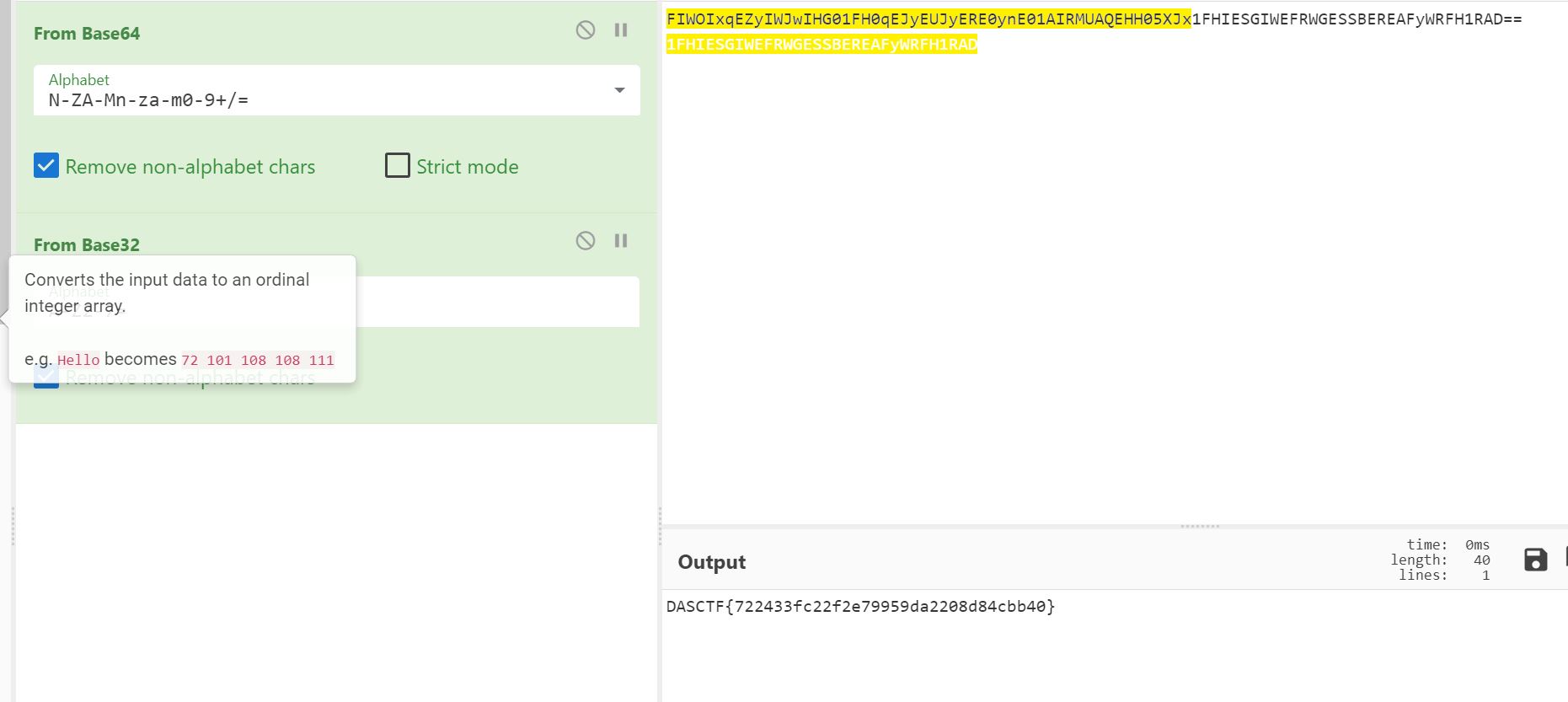
- 下载附件,010打开,文件结尾发现 base64 加密内容
FIWOIxqEZyIWJwIHG01FH0qEJyEUJyERE0ynE01AIRMUAQEHH05XJx1FHIESGIWEFRWGESSBEREAFyWRFH1RAD==
- 根据字符替换码表
N-ZA-Mn-za-m0-9+/=
base32
- flag
DASCTF{722433fc22f2e79959da2208d84cbb40}
m4a
题解
- 打开音频文件,很明显是一串摩尔斯密码,转换为 MP3,拖入 Audacity 查看波形图

1000 01 00001 00011 1000 1010 0 0010 1010 00111 11111 00001
BA43BCEFC204
- 010 查看 m4a 文件
- 文件结尾有倒置的 PK 文件,写脚本
1 | with open('1.m4a', 'rb') as rb: |
- 导入 010,运行 zip 模板删除多余内容,用 key 解压
(+w)v&LdG_FhgKhdFfhgahJfKcgcKdc_eeIJ_gFN
- 看 wp 知道这是 rot47+atbash
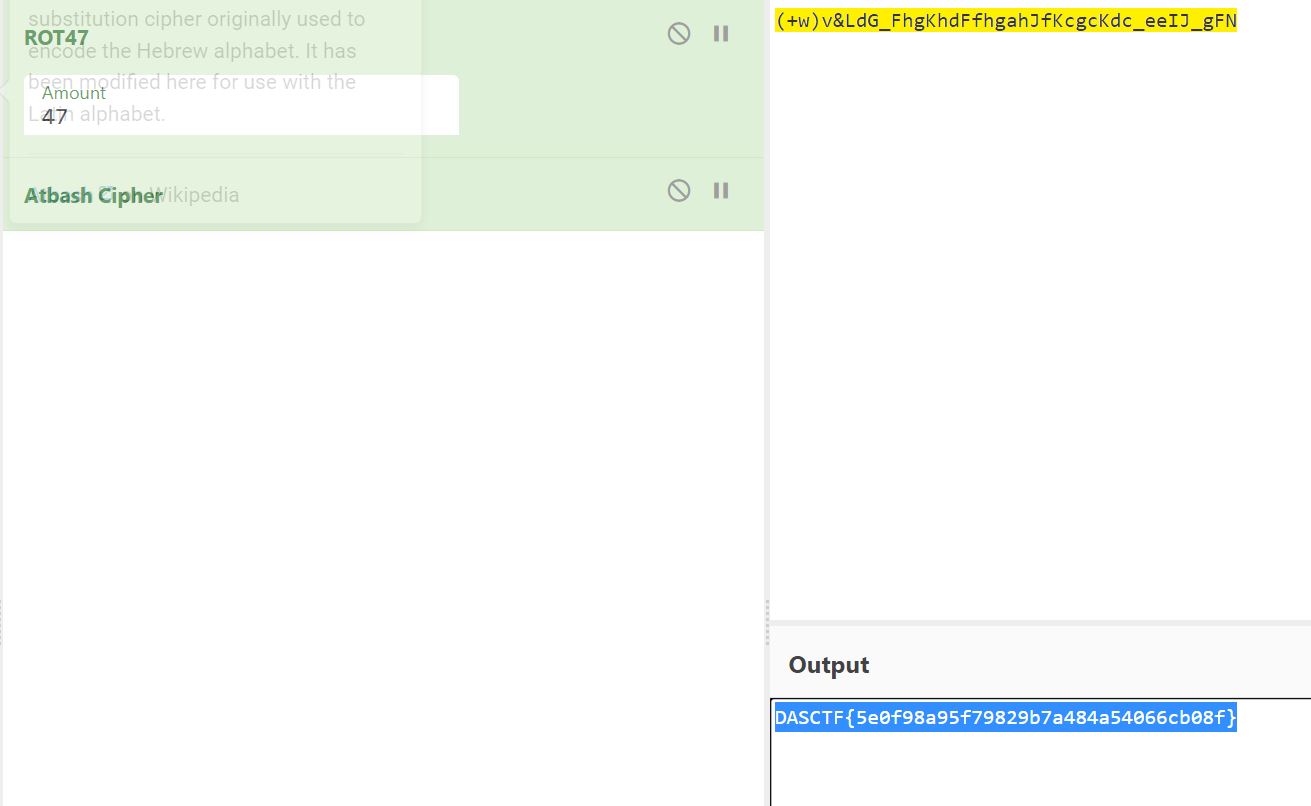
DASCTF{5e0f98a95f79829b7a484a54066cb08f}
Unkn0wnData
题解
- 010 打开,结尾有类似 base64 的文字,magic 爆破加密
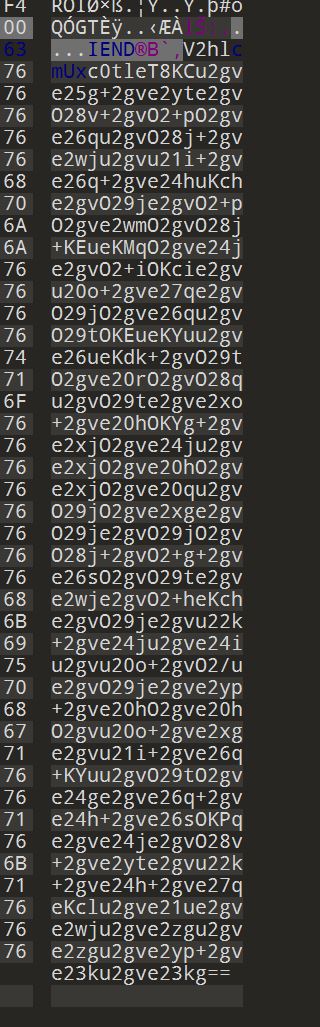
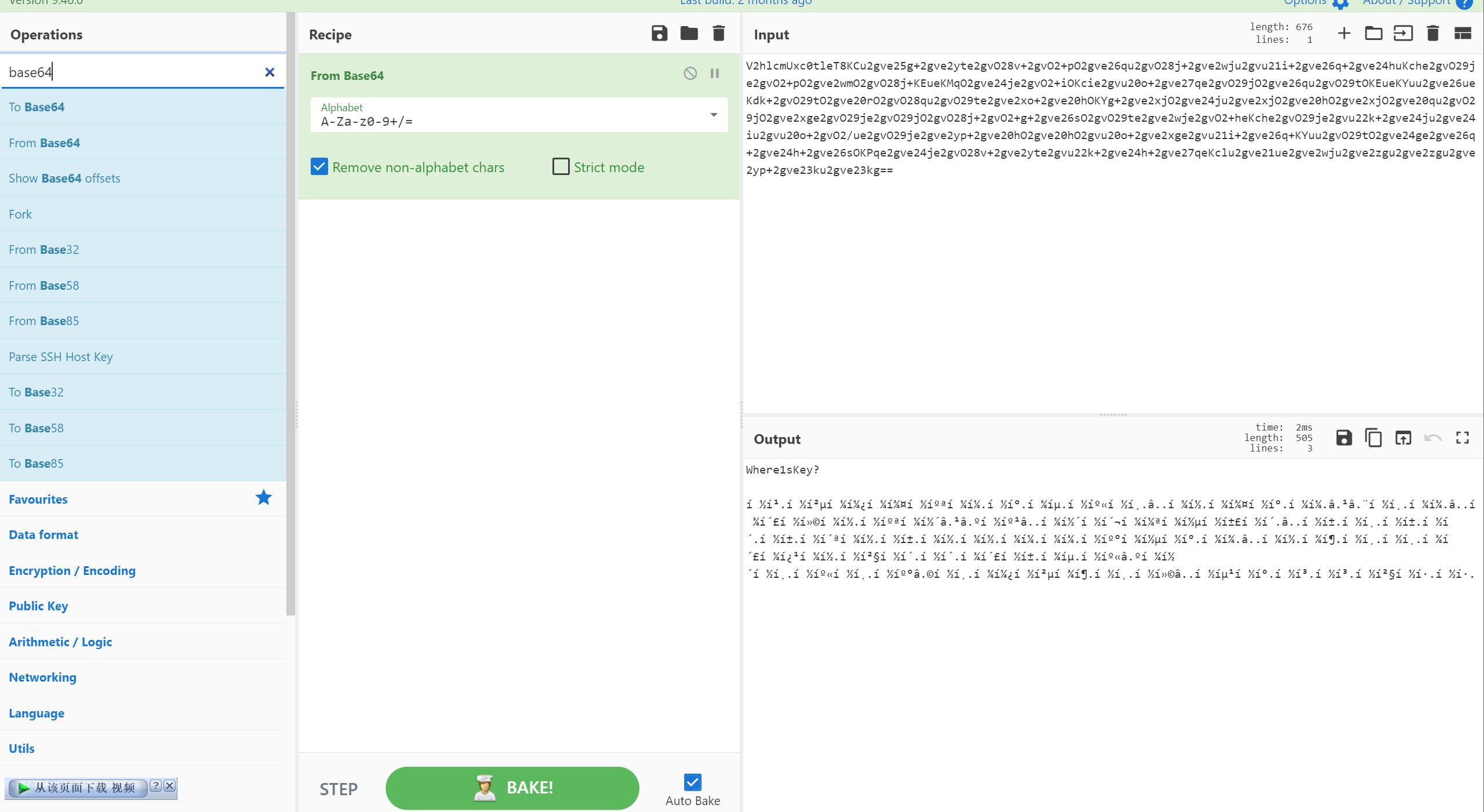

- 图片存在 LSB 隐写,保存 bin
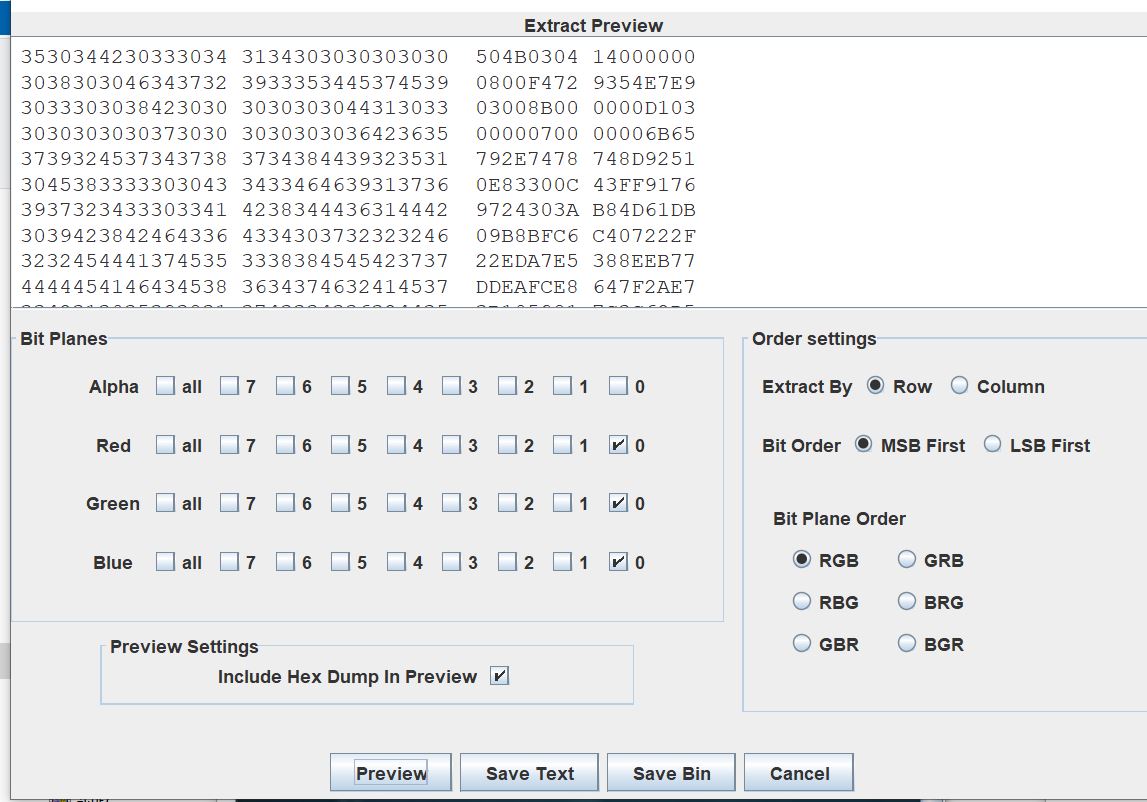
- 一个 zip,解压得到
1 | data: |
- 键盘流量(不会,先放个 0rays 的 wp
1 | normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"} |
mik
maeshiy: FindTTheoRealgKeygandlMakeeIt!d
mimashi FindTheRealKeyandMakeIt!
1 | normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"} |
key:Toggled
- emoji-aes 在线解码
- 0rays 手动解码
1 | import base64 |
U2FsdGVkX1+psEGiQ9Bl3PbdKi4mYKSHJfRIoCoRo/bepbG8tJvD+pzC53ApwRR3ekX4K0X6tZ9F2z6PxNVOOw==
- aes 解密
DASCTF{ad15eecd2978bc5c70597d14985412c4}
好怪啊
题解
- 下载附件,010打开,发现结尾处存在 kp 怀疑是倒置的zip文件
- 写代码复原
1 | a = ... # 复制的原 16进制编码 |
- 导入至010editor,保存为test.zip,解压得到 flag.png
- 发现文件头不对,修改文件头,得到正常图片
- 高度经过修改,将 25改为50,得到最终图片
- 得到flag
奇怪的棋盘
题解
- 给了一个棋盘,是典型的ADFGVX 密码所用到的棋盘,但是txt中只有11,14,21,22,51,53这六种情况,甚至没有6的出现,所以应该不是直接对应ADFGVX密码,而是对应了波利比奥斯方阵
1 | a b c d e |
- 写一个脚本转化一下
1 | b = "11,22,11,53,53,14,11,22,22,51,22,22,51,14,51,11,14,11,51,53,14,22,11,14,51,22,14,51,11,11,14,14,14,14,21,53,11,21,11,21,14,22,14,51,53,53,14,22,22,14,22,22,14,53,14,14,21,14,14,53,51,22,53,11,14,22,51,14,21,53,51,51,11,11,14,14,53,14,53,53,11,14,14,51,22,22,22,53,22,53,53,53,53,22,53,53,22,22,53,22,14,51,51,51,22,22,22,11,22,11,11,11,11,22,11,11,22,22,11,22,14,14,14,11,22,11,22,22,22,11,22,22,11,22,11,22,11,11,11,51,11,11,11,53,22,53,22,22,22,53,22,22,53,22,53,22,53,53,53,51" |
- 对图片进行 LSB 隐写分析,得到 base32 加密的 keyword
LastKey{Yusayyds}
- 得到ADFGVX密码的密文,解密
1 | key square:ph0qg64mea1yl2nofdxkr3cvs5zw7bj9uti8 |
- 解密得到 flag
hex解密:DASCTF{d859c41c530afc1c1ad94abd92f4baf8}
感谢 Artone 学长的 WriteUp
SegmentFlow
题解
- 双击打开压缩包,发现里面包含了很多小文件,可以同 crc 爆破密码
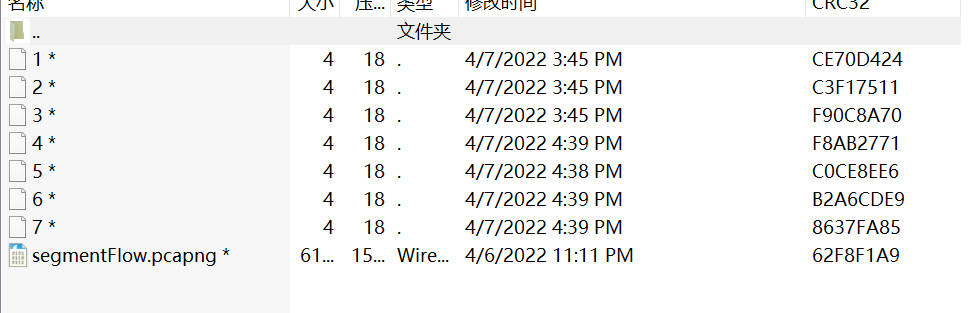
- 写代码
1 | import binascii |
password is gZinflAte_BasE64
- 解压,得到流量包
如果您喜欢此博客或发现它对您有用,则欢迎对此发表评论。 也欢迎您共享此博客,以便更多人可以参与。 如果博客中使用的图像侵犯了您的版权,请与作者联系以将其删除。 谢谢 !